Many Gmail users never touch SPF, DKIM, or DMARC — because Google takes care of behind-the-scenes technical details well enough to make sure your emails generally make it to your recipients without them.
In fact, from what I’ve found, quite a few people run away from me screaming at the mention of those three acronyms and/or have never heard of them. In the latter case, people still run away from me screaming, but that’s more due to my general dislikability than their fear of the technical side of email.
But… if you’re using a third-party SMTP server with Google Workspace — whether it’s to break Gmail’s limits with GMass or for other reasons — the email authentication acronyms really come into play.
With GMass’s DKIM settings, you can make sure your emails are DMARC compliant (in most cases) when you’re sending through an external SMTP server.
In this guide, I’m going to cover the DKIM settings inside the GMass dashboard and walk you through how (and why) to use them to hit DMARC alignment.
Note to email pros: If you want to skip through the What Is DKIM? section to jump to the setup instructions for GMass, go for it. However, I am covering some nuance in the What Is DKIM? section, including some things you might not know about which different SMTP services strip out custom DKIM headers, so you might want to give it a quick glance on your way down.
DKIM Settings in GMass: Table of Contents
- What Is DKIM?
- Setting DKIM and Passing DMARC When You Use a SMTP Server With GMass
- DKIM Settings in GMass: Next Steps
What Is DKIM?
DKIM, which stands for DomainKeys Identified Mail, is one of the three primary email authentication methods that email systems can use to weed out fraudulent and spoofed emails.
With DKIM, an email client can confirm that an email that claims to come from a specific domain was actually sent by that domain.
DKIM works by attaching a domain name’s verifiable digital signature to an email. The email system that receives that email can verify the signature against the domain name’s records to confirm its validity.
All that happens behind the scenes — so if you’re failing DKIM, you wouldn’t know without doing some investigation. (We’ll get more into that later in this article and cover how to use an email analyzer tool to check your DKIM settings.)
How DKIM relates to DMARC
DMARC, which stands for Domain-based Message Authentication, Reporting, and Conformance, is another email authentication method.
DMARC uses DKIM (and/or SPF) to authenticate emails and also gives a server instructions on what to do if an email from your domain fails both DKIM and SPF checks, or both DKIM and SPF alignment.
When DKIM (or SPF) is aligned, it lets a receiving mail server know an email is from the domain it says it’s from.
That can make a difference in deliverability (along with making it harder for people sending spam and phishing emails to spoof your domain).
Why it’s easier to pass DMARC alignment with DKIM vs. SPF
DMARC does not require alignment on both DKIM and SPF (Sender Policy Framework) — just one.
And it’s trickier for DMARC to get SPF alignment than DKIM alignment.
Why? It’s largely because SPF uses the Mail From (aka the Return-Path) domain for authentication, while DKIM uses the domain from the sender’s email address.
In order to achieve SPF alignment, the Mail From domain has to match the sending domain — which often isn’t the case when you’re using a third-party SMTP server.
The SMTP service would need to support a custom Mail From domain for every sender, which isn’t always the case — and adds a whole new layer of complexity to the setup process if it is the case.
Also, the Mail From domain requires two DNS records (MX for receiving and processing bounces and TXT for SPF authentication) while DKIM requires just a TXT record.
And with a third-party SMTP server, getting the MX record to work with that server is cumbersome and complicated — you’d need to set up a new subdomain to use as the Mail From, or else all emails sent to your main domain would go to the third-party server instead of your email account.
Plus, the subdomain means that the SPF alignment will be considered relaxed and not strict. With DKIM, there’s no messing around with a subdomain so the alignment will be strict, which is preferred.
Overall, DKIM is both more reliable and less complicated to set up than SPF — which is why it’s a better choice for DMARC alignment.
How DKIM Works When You Send Messages Through GMass Using an SMTP Server
By default, GMass sends your email campaigns through Gmail’s servers. Those are reliable, high-deliverability servers — arguably the highest-deliverability servers in the world.
However, GMass also enables you to use a SMTP server to send campaigns. That gives you the ability to break Gmail’s daily sending limits (up to 500 emails for a free gmail.com account and up to 2,000 emails for a Google Workspace account).
If you’re using a SMTP server — either your own third-party server or one of GMass’s in-house SMTP accounts — you can set DKIM in the GMass dashboard.
From there, one of two things will happen when you send your campaign.
Scenario 1
You can wind up with multiple DKIM signatures: One set by GMass and one by your SMTP server. That’s ok — your emails can have multiple DKIM signatures and still pass DMARC. It’s all good.
This scenario can happen if you’re using your own third-party SMTP service or one of GMass’s in-house offerings.
Scenario 2
Some SMTP servers strip away custom DKIM headers. (See the list next.) In those cases, if you’re using your own SMTP service, you’ll need to set up DKIM with your SMTP provider.
If you’re using one of GMass’s SMTP servers that strips DKIM, like our SendGrid server, unfortunately, you’ll fail DMARC. (Since you can’t go into our SendGrid to set your own DKIM header.) Fortunately, though, this won’t affect deliverability for most users.
In the next section of this article we’ll cover DKIM and DMARC setup steps.
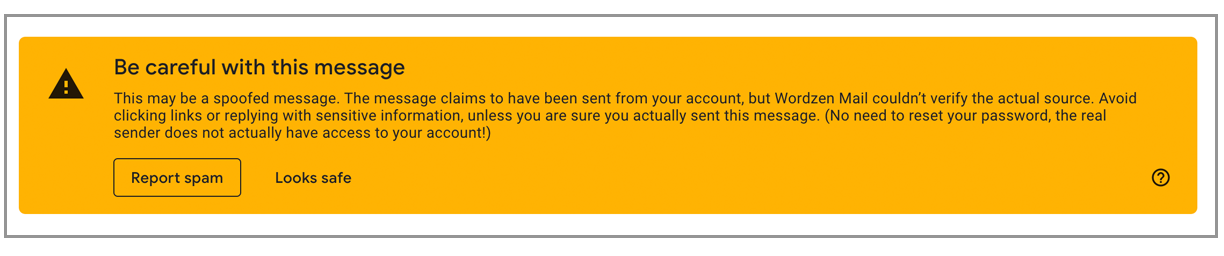
A note to free gmail.com email users: While you can send messages from a gmail.com account through an external SMTP server, you’ll fail DMARC since it’s impossible for you to set up DKIM for a domain (gmail.com) you don’t own.
However, the gmail.com DMARC record tells servers not to punish the email for failing, so it will still go through. And in our tests, the messages hit the inbox. (Though some carried the frightening Google warning that “This may be a spoofed message.”)
Which SMTP services strip out custom DKIM headers and which don’t
Here are the results of our testing on which popular SMTP services strip away custom DKIM headers and which don’t.
Here are the popular services that do and don’t strip custom DKIM headers:
- SendGrid – strips out your custom DKIM header
- Amazon SES – keeps your custom DKIM header
- ReachMail – keeps your custom DKIM header
- JangoSMTP – strips out your custom DKIM header
- GMass’s own server, SMTPGM – keeps your custom DKIM header
Now it’s time to set everything up the right way in GMass (and/or your third-party SMTP service).
Setting DKIM and Passing DMARC When You Use a SMTP Server With GMass
Here’s what you need to do to set up DKIM to pass DMARC when you use a SMTP server with GMass.
First: Are you using one of GMass’s SMTP servers or your own third-party server?
If you’re using GMass’s SMTP servers
In case you didn’t know, GMass has accounts with some SMTP services, as well as an in-house homegrown SMTP server, which some GMass users can access.
You can apply to use GMass’s SMTP services if you send opt-in emails and you have a reliable sending history and reputations.
Before… if you used GMass with one of our in-house SMTP accounts, it was impossible for your emails to be DMARC compliant.
They would pass SPF and DKIM… but they would fail DMARC alignment (if you had a DMARC record published, of course). While that didn’t affect deliverability for most users, it could… plus it could lead to Google’s spoofing warning.
But with our new DKIM abilities, that’s no longer the case.
With GMass’s DKIM settings now, you can make sure your emails are DMARC compliant or DMARC ready in most cases when using an external SMTP server.
If you’re on GMass’s own SMTPGM server, Amazon SES account, or ReachMail account, they’ll preserve your custom DKIM settings and, assuming all is set up correctly in your DNS records, you’ll pass DMARC.
If you’re on GMass’s SendGrid account, since SendGrid strips DKIM, you’ll fail.
But regardless, we always recommend setting up DKIM in the GMass dashboard if you’re going to use SMTP for sending. (That way, if your SMTP service changes in the future, you’ll hit DMARC alignment.)
If you’re bringing your own server
If you’re using your own third-party SMTP server account, there are other options.
If your service is one that preserves the DKIM headers that GMass passes along (services like Amazon SES and ReachMail), you should set up DKIM in the GMass settings.
If your service strips out DKIM headers (SendGrid, for example), you’ll need to set up DKIM at your SMTP provider.
However, we still recommend setting up DKIM in GMass in case you use a different provider in the future or your service decides to stop stripping our DKIM headers.
Setting up DKIM and DMARC with GMass
I’m creating these instructions under the assumption that you have an SMTP service set up in GMass, either one of GMass’s internal servers or your own third-party server.
(If you haven’t set one up yet, you can do so in the GMass dashboard, in the SMTP Server section.)
Now let’s set up DKIM.
Create your DKIM entry in GMass
Go to the GMass dashboard for your account.
Click the gear icon in the top right for Settings. Then click Email Authentication on the left fly-out menu and choose Manage DKIM Settings.
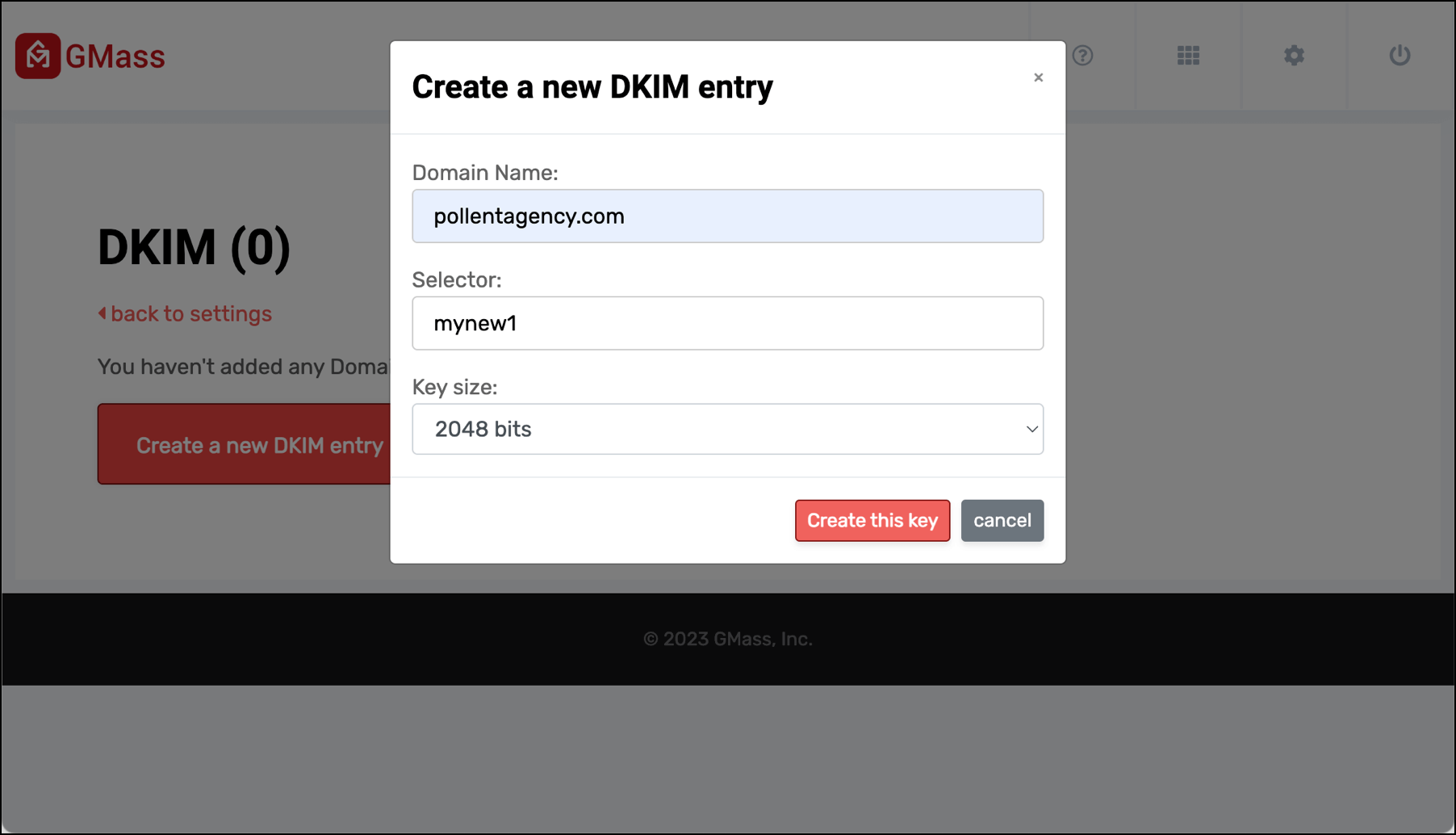
Click the Create a new DKIM entry.
Type in…
- Your domain name (in my case for this example, pollentagency.com)
- Your selector (this can be anything you want, I went with mynew1)
- And the key size (in my case, 2048 bits, but double check with your domain provider).
Then click the Create this key button.
Now click Key Details.
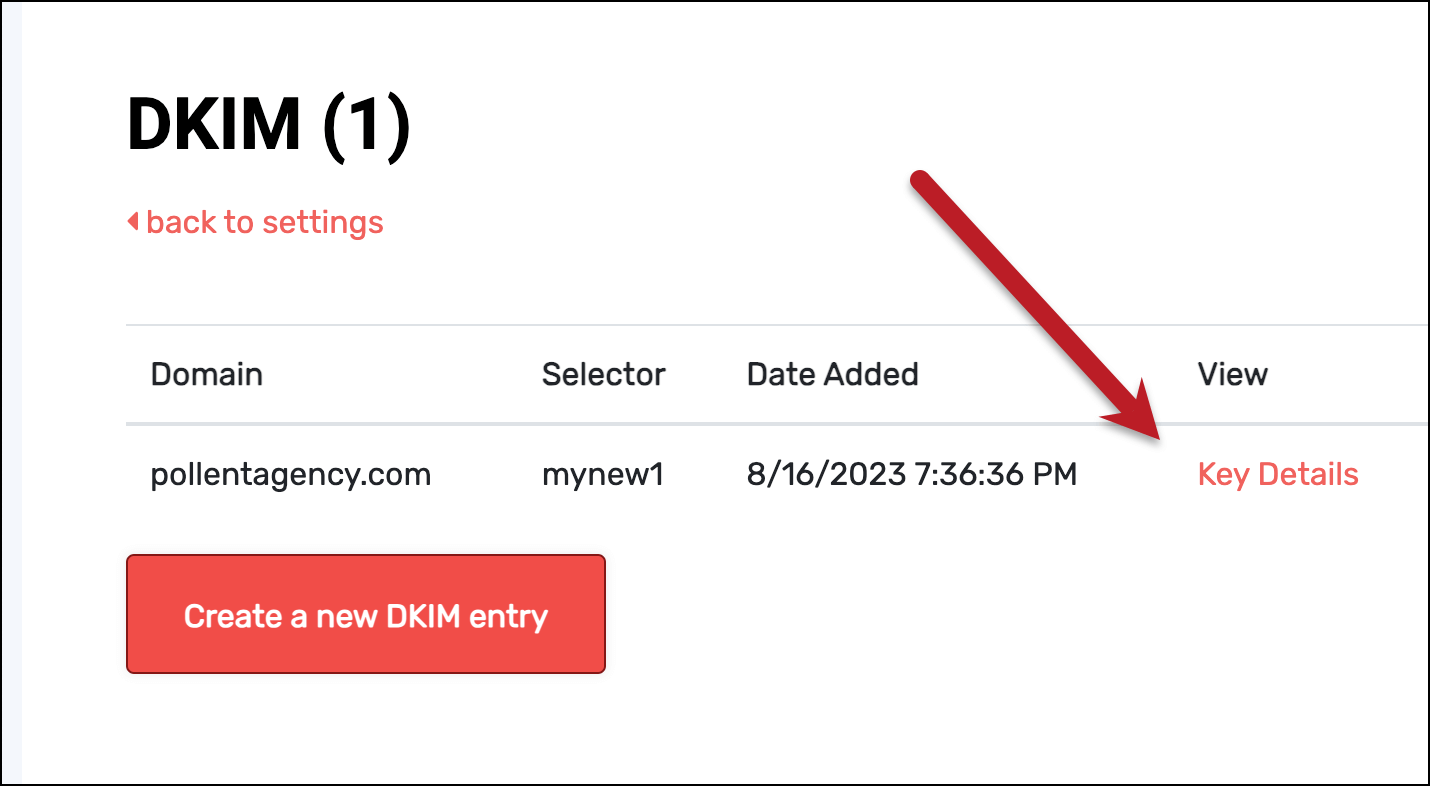
You’ll need to grab DNS Record (in my case, mynew1._domainkey.pollentagency.com) and the DNS Record Value (a long string that starts with v=DKIM1).
Creating the DNS record for your key
Go to your domain registrar and go into the DNS settings for your domain. (Where you’ll find those settings varies at every domain registrar, but generally they’re easy enough to track down.)
Create a new DNS record, and for the type of record, you want TXT.
The host name should be selector._domainkey.yourdomain.yourdomainsuffix. Then for the data/value section, paste in the long text string GMass generated; it should start with v=DKIM1.
Save the settings at your registrar.
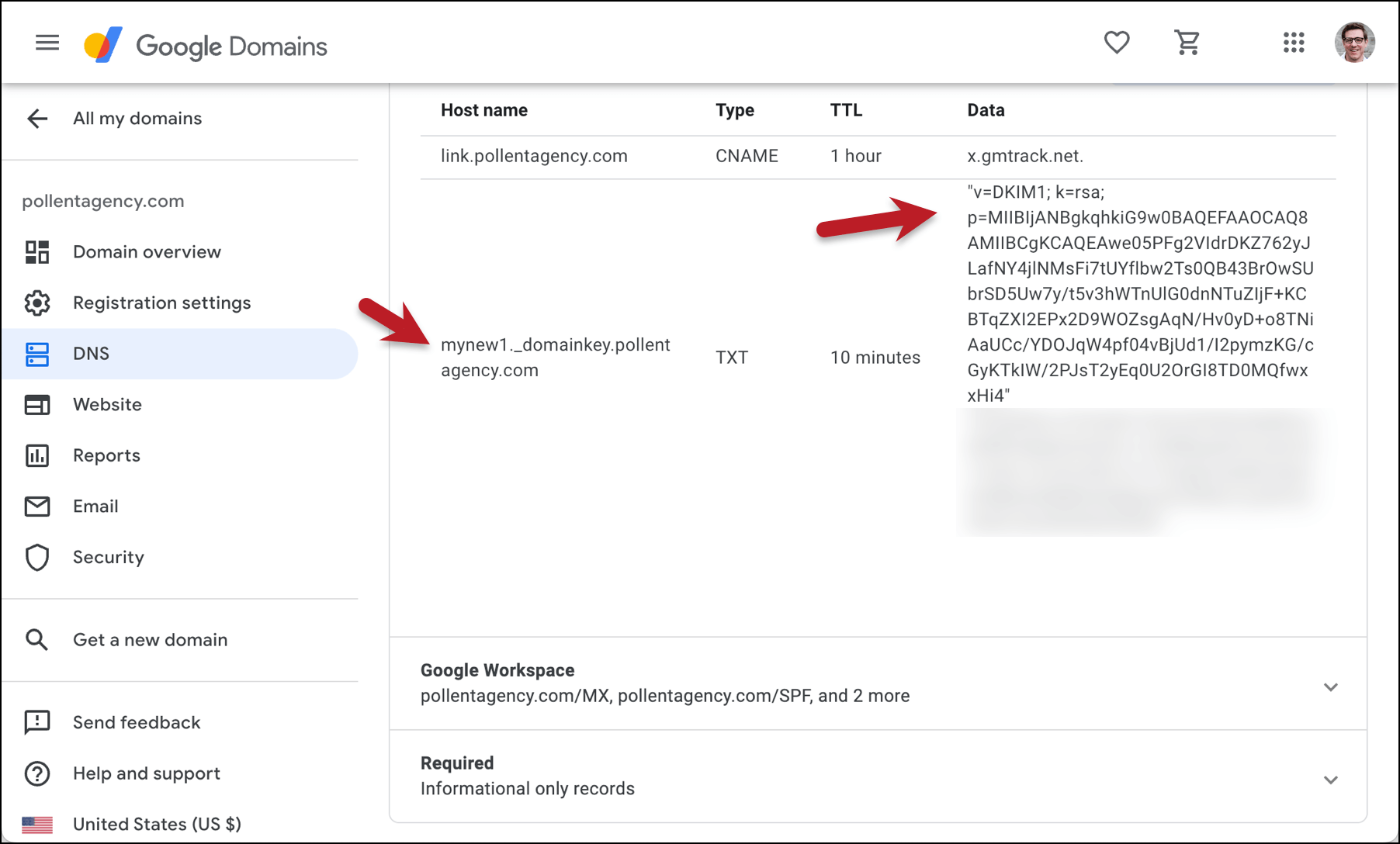
Authenticate the record in GMass
Go back to the DKIM settings in the GMass dashboard and click the link to Active this key. You may need to give this some amount of time for the DNS record to propagate.
Once your new DNS record has propagated and you hit the Active link, GMass will give you a success message.
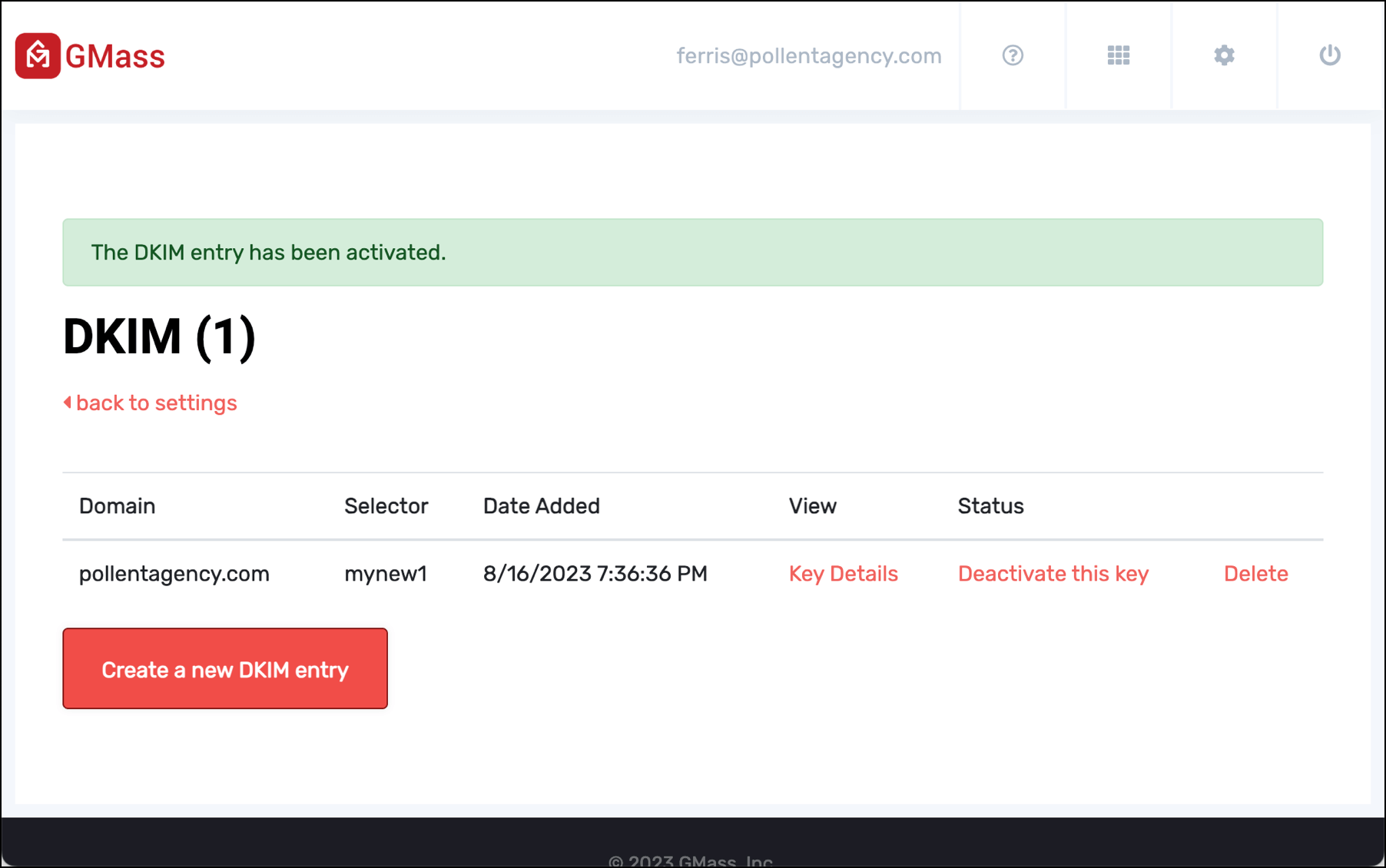
If you’re using your own third-party SMTP server and it’s one (like SendGrid) that strips out DKIM headers, this is when you’d go to your SMTP provider and set up your DKIM record there.
If your own third-party SMTP server retains the DKIM headers it receives from GMass (like Amazon SES), you don’t need to also set up DKIM there.
Create your DMARC record
Now you can create a DMARC record for your domain. I used this DMARC Record Wizard to create mine, though you can probably just adapt yours from what I did.
I went with Strict authentication for DKIM.
Now go back to your domain registrar, create another new TXT record, and enter your DMARC settings.
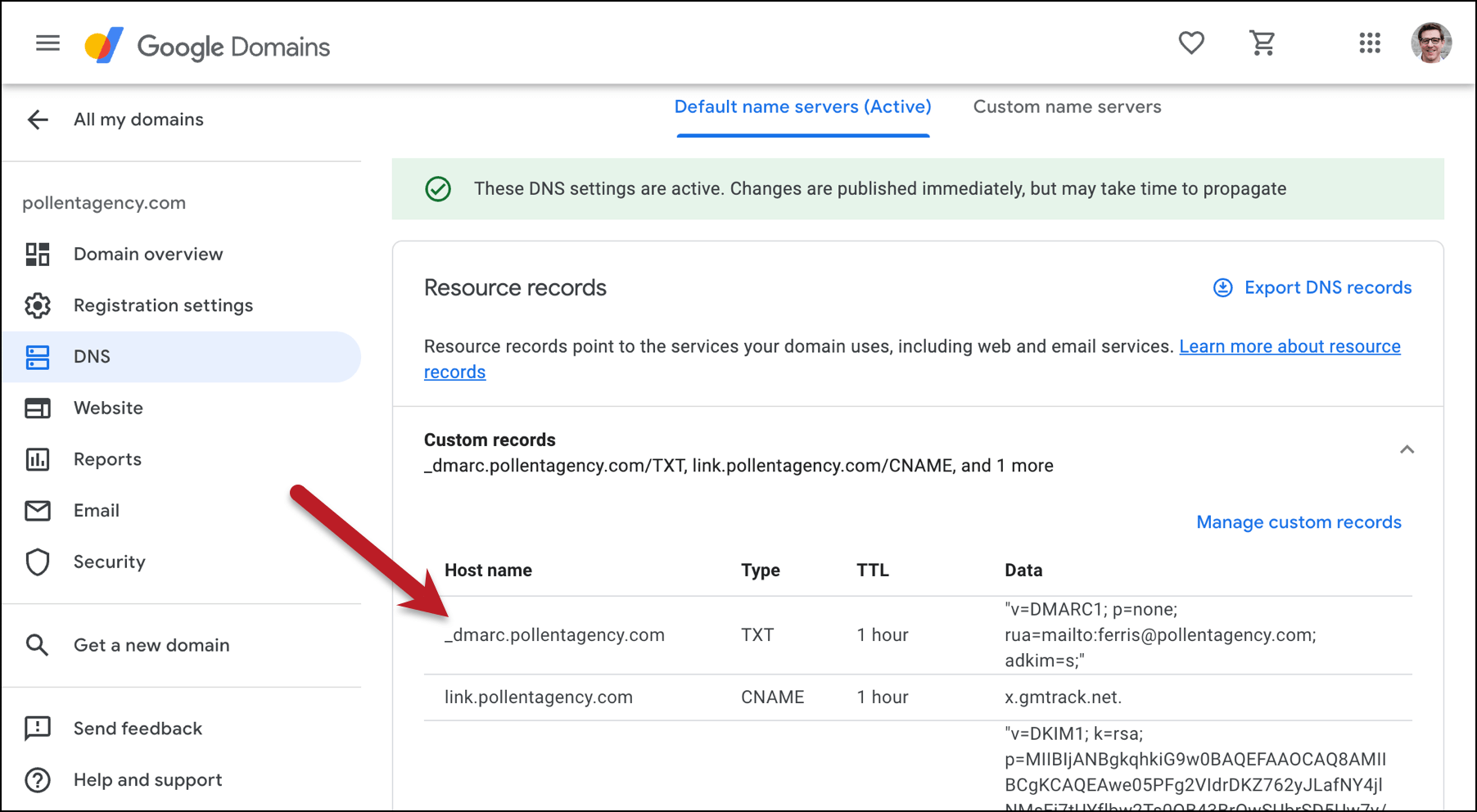
Once again, it may take a bit of time for the record to propagate.
Testing your DKIM headers and whether you’re passing DMARC
Once you’ve set everything up — and given it some time for all your records to propagate (this is definitely my personal record for uses of the word “propagate” in one article) — it’s time to run a test.
Head to GMass’s free Email Analyzer tool, which shows you all the underlying technical info about your email.
Copy the testing email address you see on the screen.
Then go to Gmail. Compose a new email and paste in the testing email address in the To field.
Open the GMass settings box and under Action, make sure your SMTP server is selected.
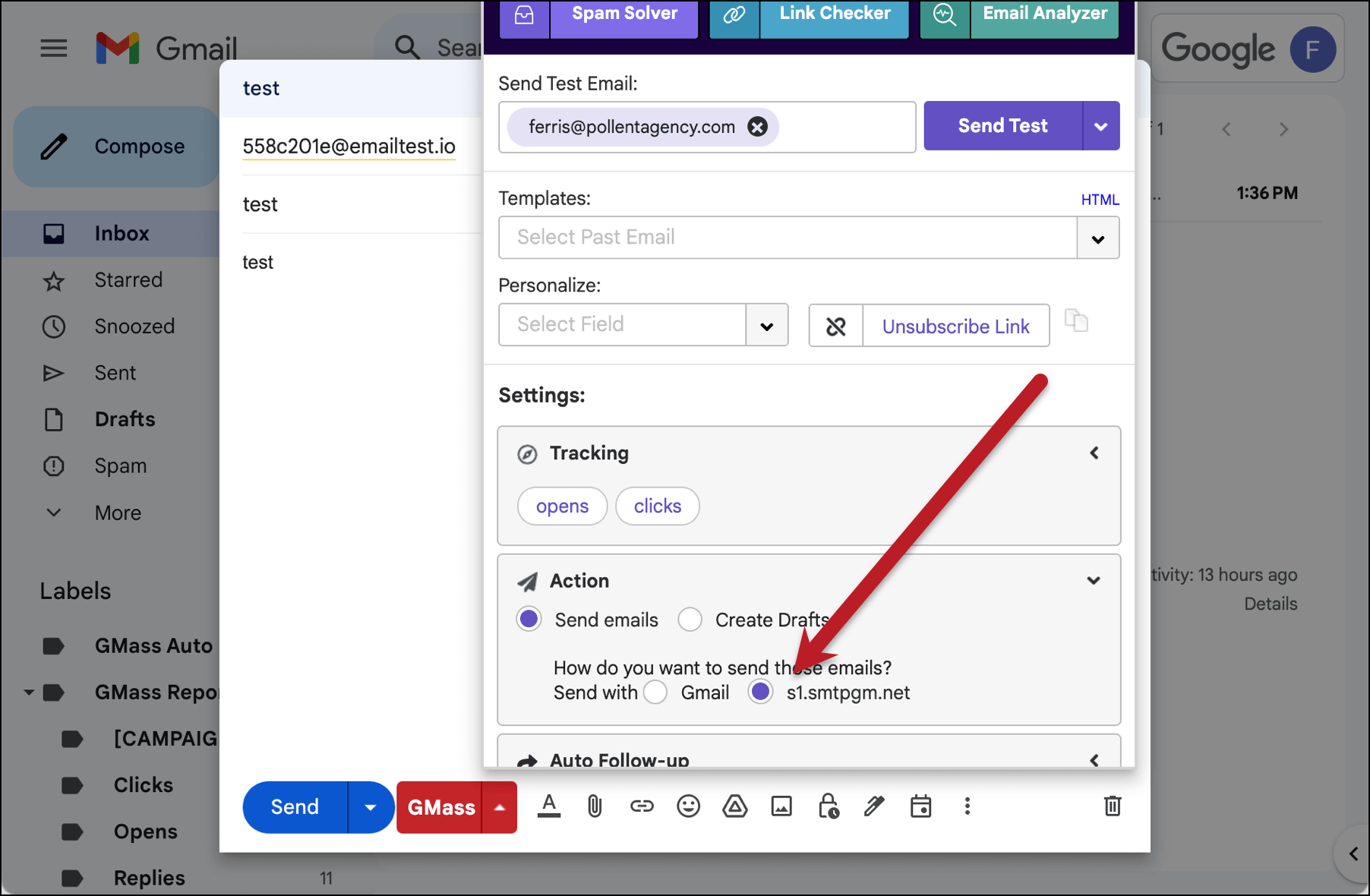
You can type in anything as the subject and body (I put “test” in both), or leave them blank.
Then hit the GMass button and NOT the blue Gmail Send button to send your message through your SMTP server.
Go back to the Email Analyzer. Once it receives the message, it will show you all the behind-the-scenes technical info about your email.
You can see the DKIM headers from your SMTP service and, assuming your SMTP service retains the DKIM header you just created, that one as well. Since I sent my email using GMass’s in-house SMTP server, which retains DKIM, I see both headers.
(And again, as I mentioned before, multiple DKIM headers for an email are not a problem.)
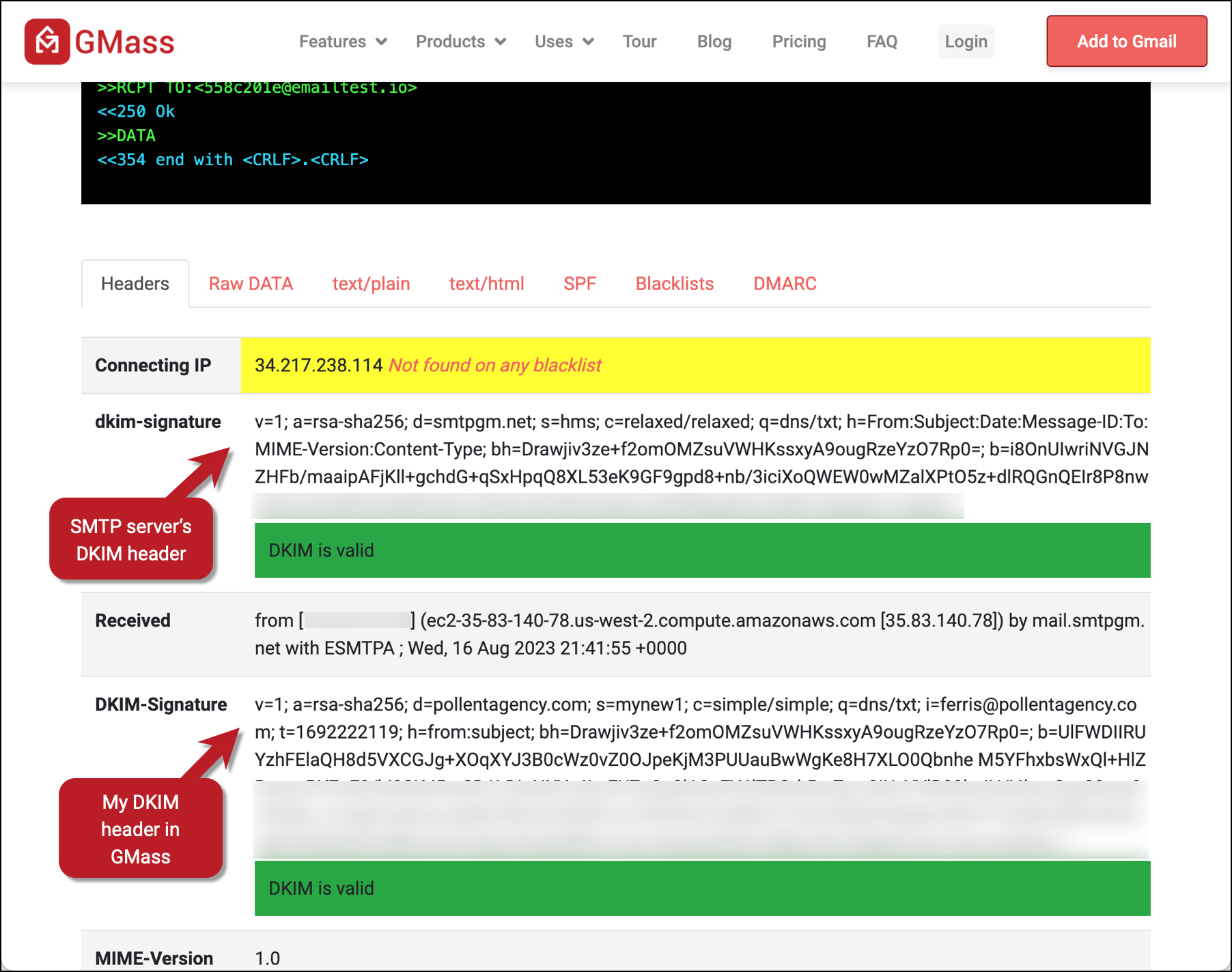
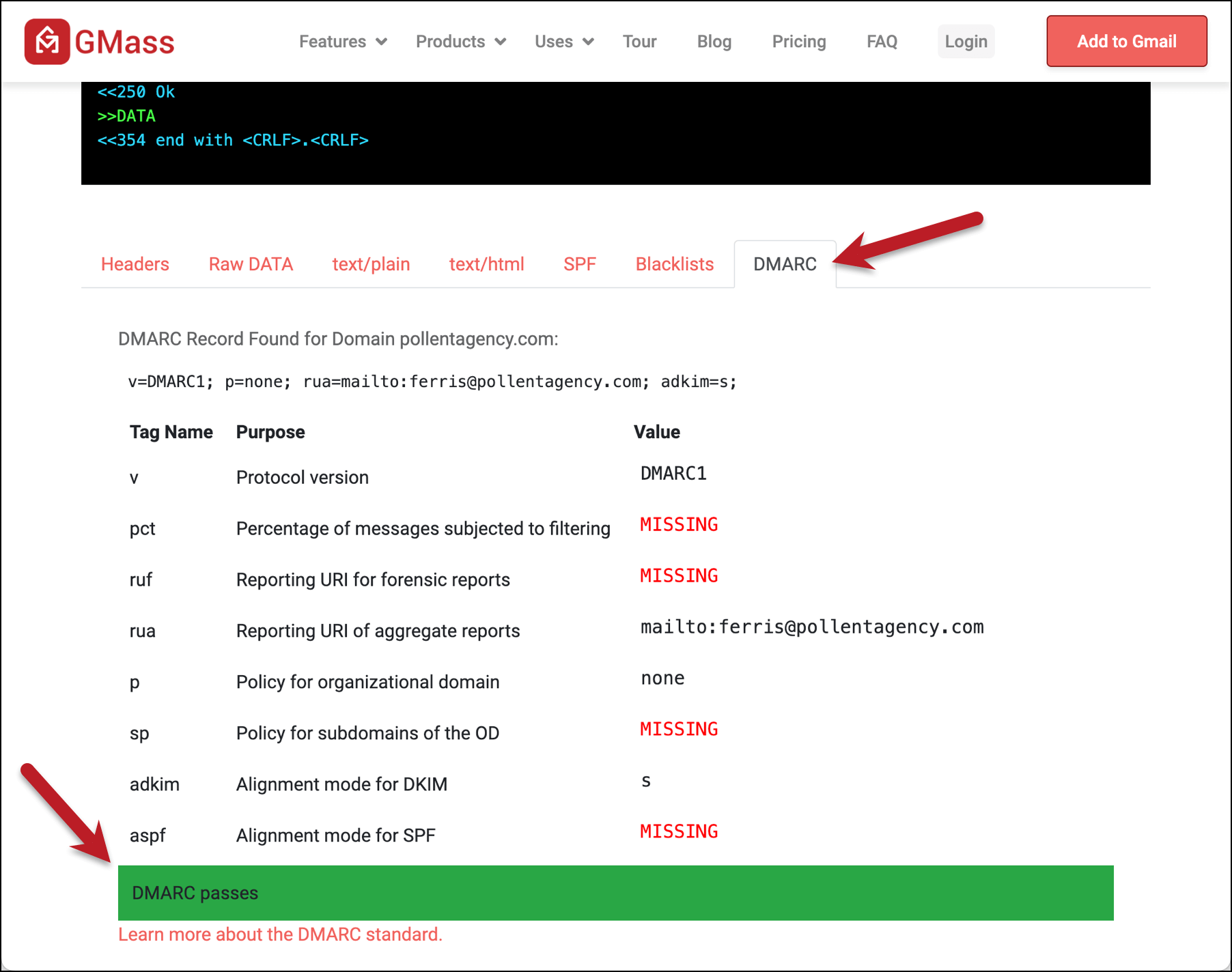
And when one of the DKIM headers is aligned, you’ll see a successful result in the DMARC section of the report.
DKIM Settings in GMass: Next Steps
If you’re going to use a SMTP server to send messages in GMass, we recommend you set up DKIM and aim for DMARC alignment.
Even if you’re using a SMTP server that strips out the DKIM header you pass along, it’s still wise to set up DKIM now in GMass. That way if you change SMTP servers or they change policies, your working DKIM will already be in place.
And if you’re not a GMass user yet… give it a try! You can get started for free by downloading the GMass extension from the Chrome Web Store. It takes less than a minute to get set up and there’s no credit card required for the free trial — you don’t even have to fill out a form.
Email marketing. Cold email. Mail merge. Avoid the spam folder. Easy to learn and use. All inside Gmail.
TRY GMASS FOR FREE
Download Chrome extension - 30 second install!
No credit card required


