Earlier I wrote about my feelings on Google’s new verification process for sensitive and restricted Gmail API scopes, and here I’ll be posting live updates of GMass’s journey through the process. We’re doing this for the benefit of the thousands of developers that have yet to begin the process, are thinking about the process, or are frustrated with the process.
1/25/2020
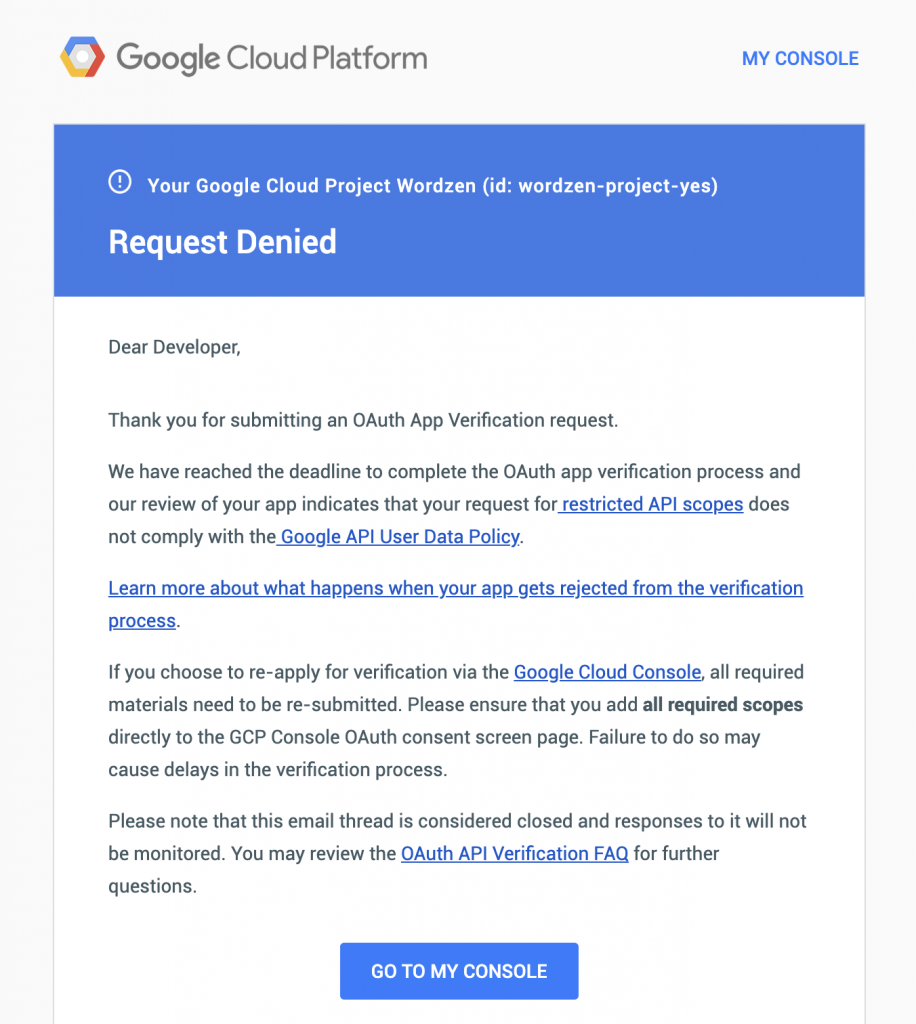
In my previous update on 1/5/2020, I mentioned that Wordzen, by some miracle, had managed to still have full access to the omnipotent https://mail.google.com scope despite skipping the security assessment. I spoke too soon. On January 13, I received word that the project had been reviewed, and my access to that scope was no longer.
1/5/2020
Due to time constraints and wanting to keep my sanity, I haven’t posted live updates in a while, though much has happened. since August of 2019. I’ll attempt to summarize what’s happened lately, in this final update.
GMass was approved and issued the Letter of Assessment from Leviathan in October. Google then approved the restricted scopes that GMass needed to operate.
Also in October, Google announced that developers using the Google Sheets v3 API would need to migrate to v4, necessitating a new OAuth verification procedure, one that I’m still navigating.
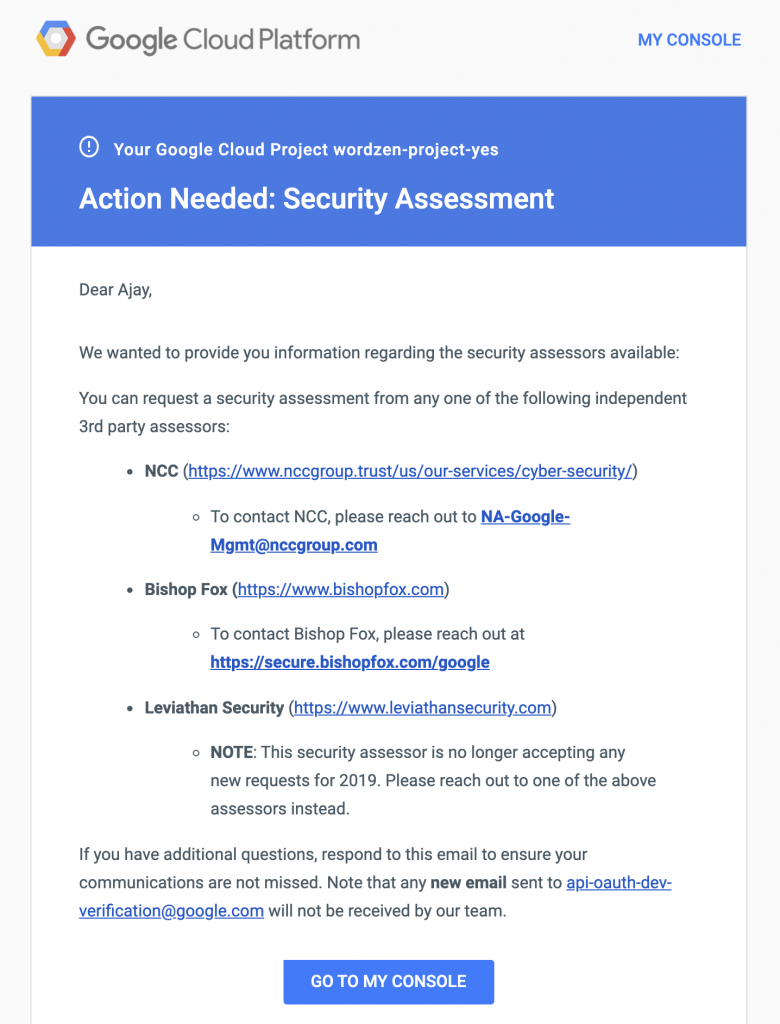
In addition to GMass, I have two other apps that use restricted Gmail API scopes, Wordzen and SearchMyEmail.com. After Leviathan completed the assessment of GMass in October, I asked if they would now review Wordzen. Wordzen is a much simpler app than GMass and because I now had the knowledge of what a security assessment is, I figured Wordzen would be much easier. Unfortunately, Leviathan told me they were too busy to review Wordzen.
I considered engaging Bishop Fox or the new assessor, NCC, for Wordzen and SearchMyEmail, but because both of those apps are non-revenue-generating, I decided against it and to let those apps remain “unverified”, which comes with some interesting quirks.
In mid-November, Leviathan contacted me. Even though I had passed the security assessment, they needed to ensure that I had a Vulnerability Disclosure Program set up. As a result I created the URL gmass.co/incident and added this to the footer of the GMass website.
For SearchMyEmail.com, in June/July I had a lengthy back and forth with the OAuth team. I was at the stage where a security assessment was required, and I informed them that I would not be undergoing the assessment, would happily remain “unverified” and that I would just remain under the 100-user unverified app limit. I had planned to do this by revoking inactive tokens and forcing users to re-auth periodically. However, I found that Google’s counting of active tokens was flawed, and after complaining enough, they increased my limit from 100 tokens to 200 tokens.
For Wordzen, the outcome was different. After being sent multiple emails informing me I must undergo the security audit, I wrote back, noting that there are only 25 active users for Wordzen, and since I’m under 100, if Wordzen could continue operating that way. They responded with this detailed explanation which put my concerns at rest. Additionally, in a Google OAuth miracle, as of 2020, the Cloud Console for the Wordzen project is showing the full https://mail.google.com scope as an officially approved scope for the Wordzen app. I don’t know how that happened — Wordzen never went through the security audit.
10/21/19
Looks like Google has added a third security company, NCC, that can perform a security assessment. Also, Leviathan is no longer accepting new projects for 2019.
8/26/19
The security assessment officially kicks off. On the first day of testing, Leviathan finds a SQL injection issue which they determine is critical. I fix the issue later that evening and report this to Leviathan who then marks the issue as “resolved”.
8/19/19
I create the Slack channel and invite all the relevant members from Leviathan. My first big to-do is to send them a list of all URL endpoints for the GMass Chrome extension. Since a Chrome extension is by nature, public, the endpoints can easily be grepped from the extension’s JavaScript.
8/14/19
I have my external alignment phone call with Leviathan. Because I’m essentially the sole developer of GMass, it’s just me from GMass, and one rep from Leviathan. He walks me through the process, collects some contact information from me, advises me what to do if their testing causes any technical issues on my end, like downtime, and gives me a timeframe of a few weeks to get everything done. On this call, I’m told that they’ve performed “tens” of assessments so far, and that no vendor has been unable to pass yet, which sets my mind at ease. Surely though, some software companies probably opted to not even begin the process due to cost. It’s also decided on this call that I’ll set up a private Slack channel for myself and a few members from the Leviathan team to coordinate activities related to the security assessment.
8/1/19
I finally receive information on the “external alignment” meeting with Leviathan, which will be the first step in the security assessment.
Within minutes I respond and request the first available time slot, which is August 14th at 1 PM PST.
7/29/19
It’s now been 5 days since I sent back the signed contract for Leviathan and haven’t heard anything further, so I follow up.
…and I hear back a few minutes later.

7/24/19
After not hearing back from Leviathan, I followed up on July 23rd, and did receive this response today.
A few minutes later, I received the official proposal. For privacy purposes, I won’t post the proposal here, but suffice it to say, it’s a standard contract with a quote, and there’s nothing specific to the security assessment of GMass in this proposal. The effort is scoped at a 3-day effort at a particular USD rate per day.
I sign and send the contract back on this same day.
7/22/19
After making some substantial security enhancements to our entire infrastructure, I reach out to Leviathan telling them that I’m ready to begin the security assessment.
6/25/19
Bishop Fox updates me again with some more information, including a What to Expect document for the security assessment. This document doesn’t contain any sensitive information, so I’m making it available for download.
I let Bishop Fox know that I’ll be reviewing the information and then letting them know if I want to proceed.
6/21/19
I’m told that the Self Assessment Questionnaire from Bishop Fox has been approved!

6/4/19
My contact at Bishop Fox updates me again on the status of the SAQ approval with Google.
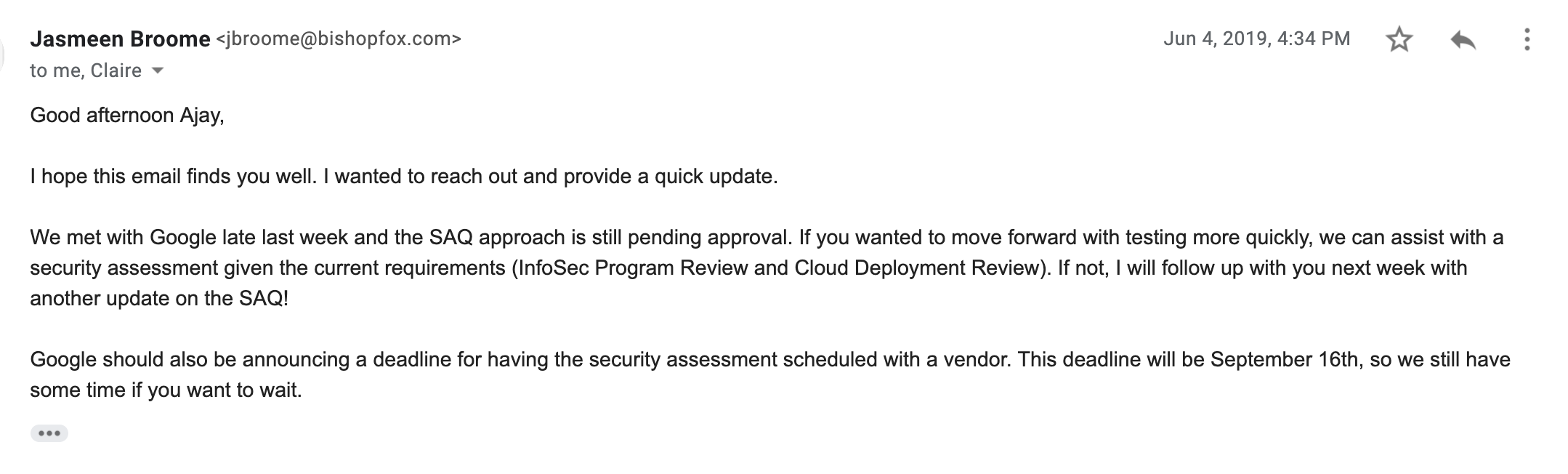
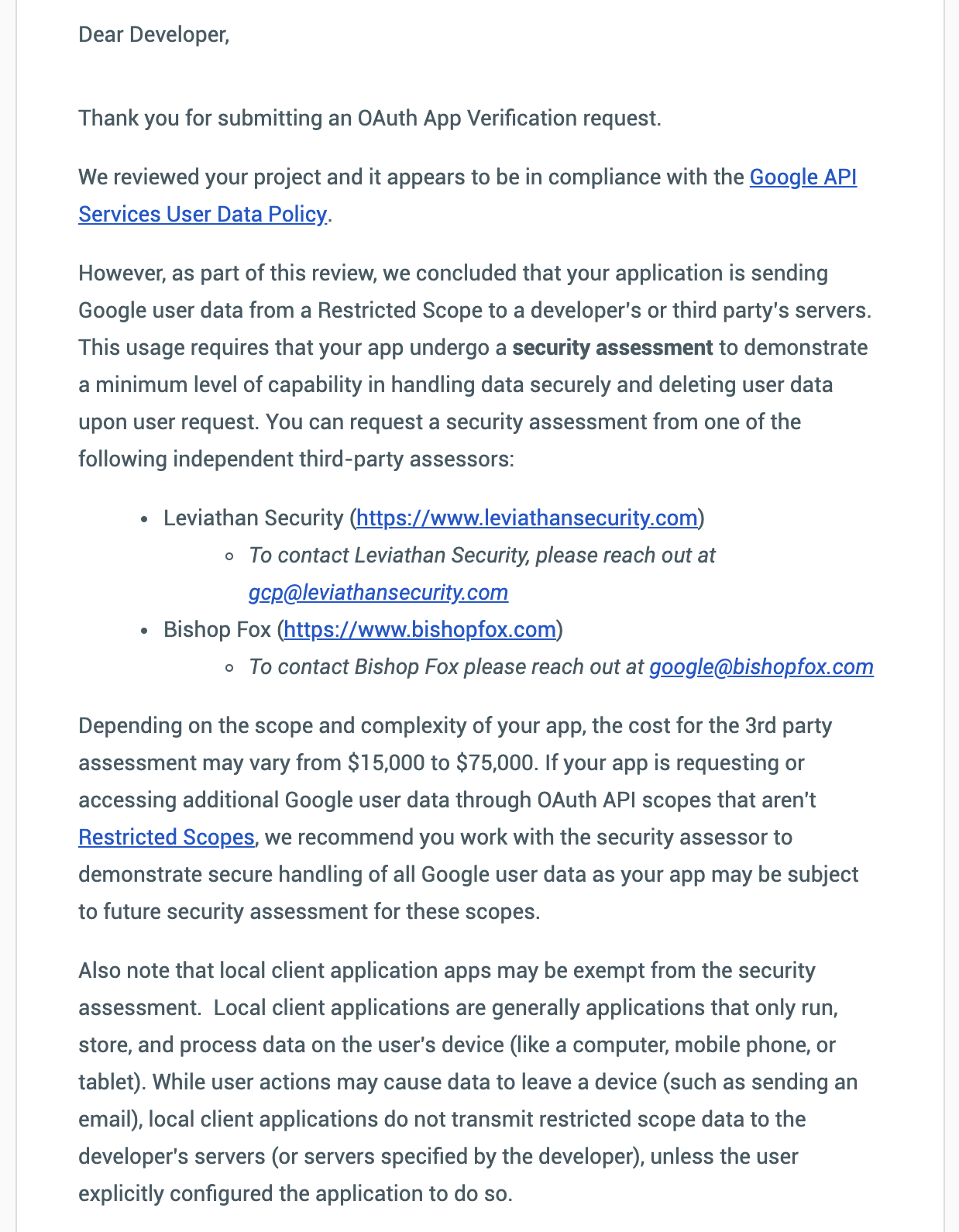
What I find most interesting about this email is the mention of a deadline to have the security assessment scheduled. There’s never been any mention of this in the documentation from Google or my correspondence with the Google OAuth team.
5/28/19
I email Bishop Fox to ask about the approval status of the SAQ (Self Assessment Questionnaire), because it’s been a couple weeks and I haven’t heard anything. If Google approves their use of the SAQ, it lessens my cost of the security assessment.
My contact responds a few hours later.
5/16/19 (update from Google)
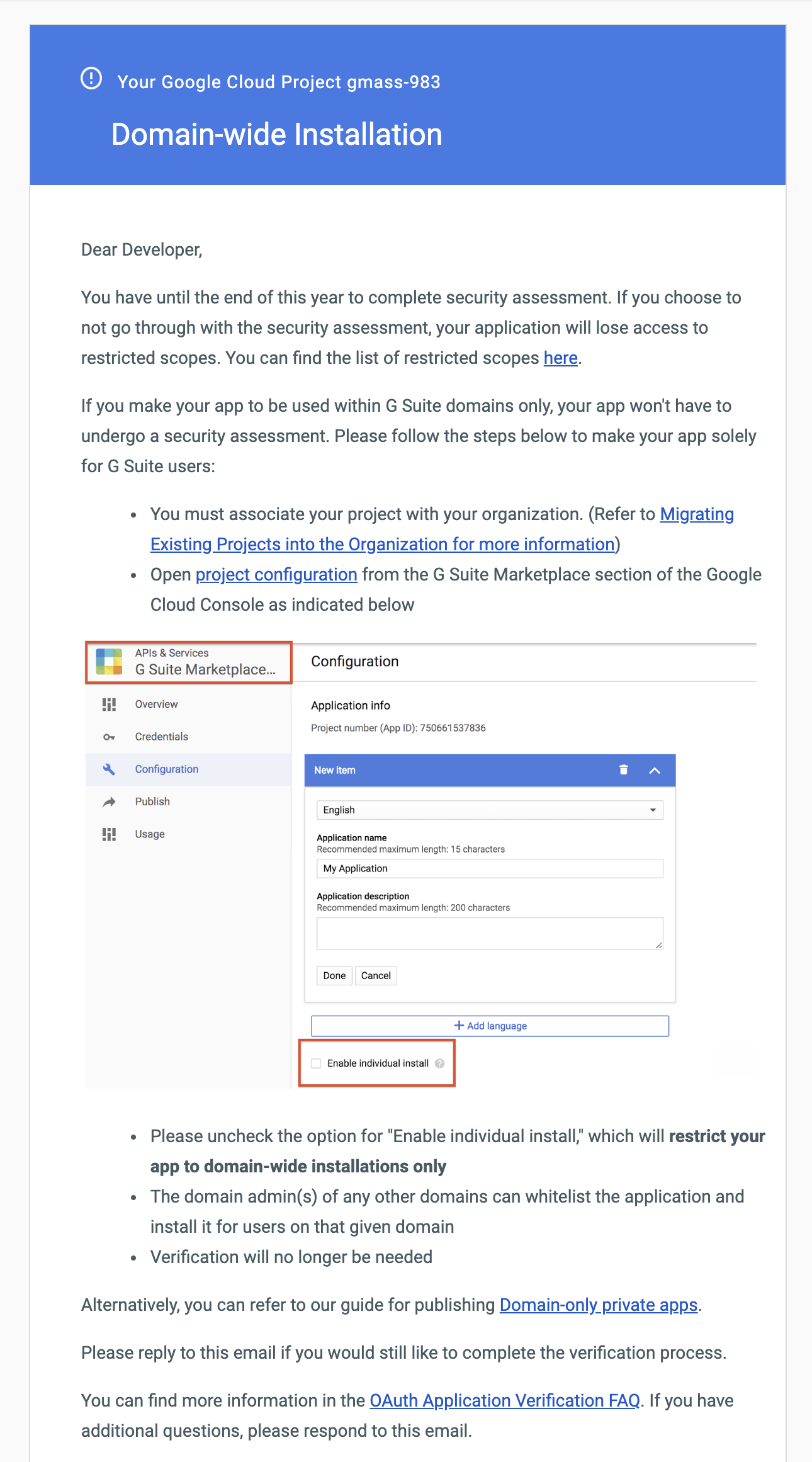
Google sent the below email, informing me that if I don’t go through with the security assessment, I’ll lose access to the restricted scopes. It also clarifies one of the prior points of confusion — that if my app is to be used within G Suite domains only, then I don’t have to go through the security assessment. Meaning, if I don’t care about taking on @gmail.com users, then I don’t need to go through with the assessment. The email also asks for confirmation of whether I will be proceeding or not. I have replied confirming my intention to go through with the assessment.
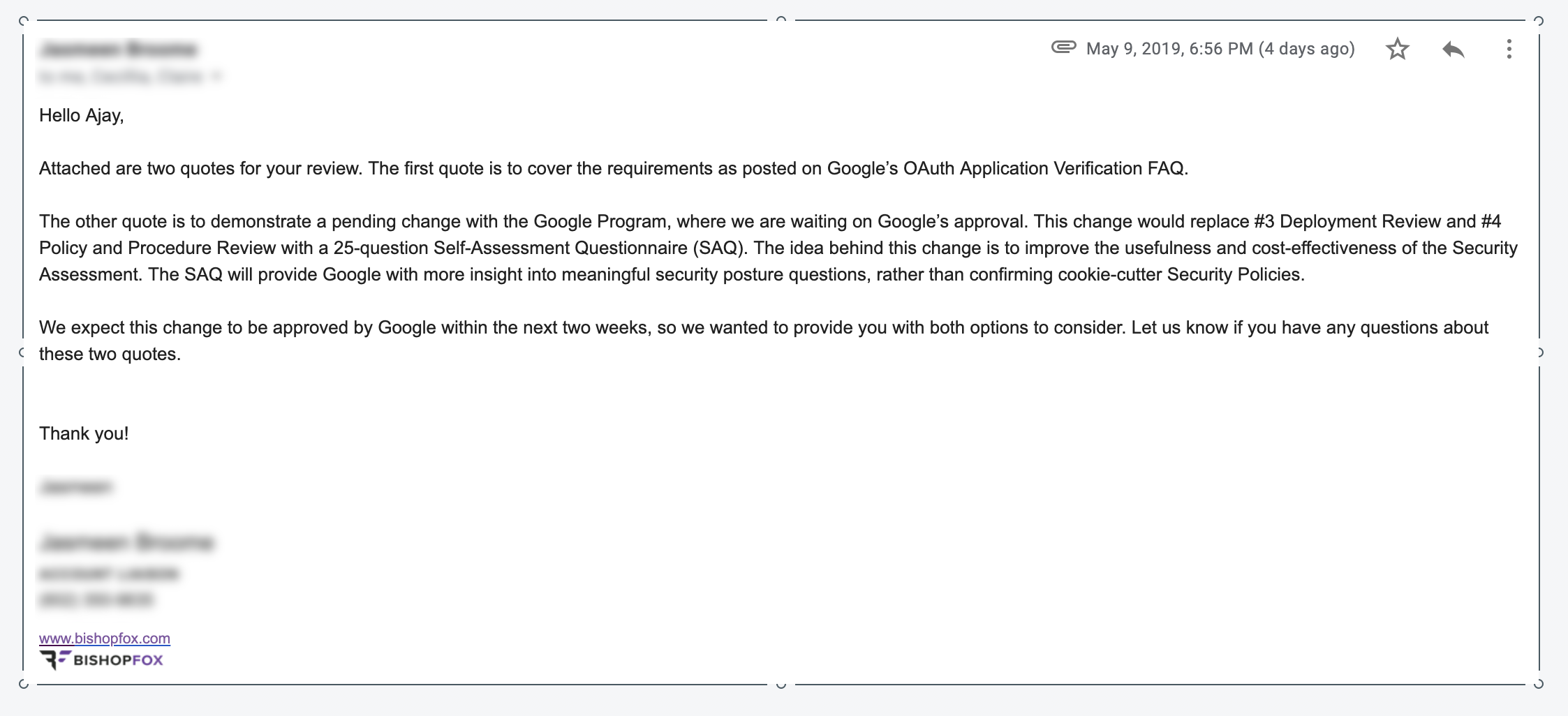
5/9/19 (two quotes arrive from Bishop Fox)
Bishop Fox explains that they are attempting to get approval from Google to satisfy one portion of the requirements via a “Self Assessment Questionnaire” rather than a full deployment review, and policy and procedure review. Of course, I welcome the simpler approach, and I’m waiting to see if this approach is approved.
5/3/19 (later that day)
Bishop Fox acknowledges receipt of the scoping survey.
5/3/19 (I respond to Bishop Fox’s scoping survey)
It took a while to fill out, because of the detailed questions in it.
5/2/19 (Proposal arrives from Leviathan)
I’m impressed with the speed at which Leviathan handles communication. It was just 15 minutes before I got a response to my initial inquiry, and I have a proposal the very next day after our phone call. I’ve been asked not to disclose pricing information, so out of respect for Leviathan, I won’t mention that here.
5/1/19 (Call with Leviathan and follow-up)
I have a short phone call with a rep from Leviathan, where I describe the nature of GMass, its public facing interfaces, and a little about its underlying architecture. Given that GMass does not have an API and is only usable as a Chrome extension, the rep indicates that this will be one of their simpler security assessments and would require 2-3 days of work. After the call, he sends me some information to verify and an NDA, which I send back the next morning.
4/29/19 (several hours later)
Bishop Fox responds within several hours of my email.
4/29/19 (15 minutes later)
Leviathan responds within 15 minutes of my email. We eventually schedule a phone call for mid-next week.
4/29/19 (later in the day)
I reach out to both of the security firms, Leviathan Security and Bishop Fox, that have been approved to conduct the security assessment.
4/29/19 (earlier in the day)
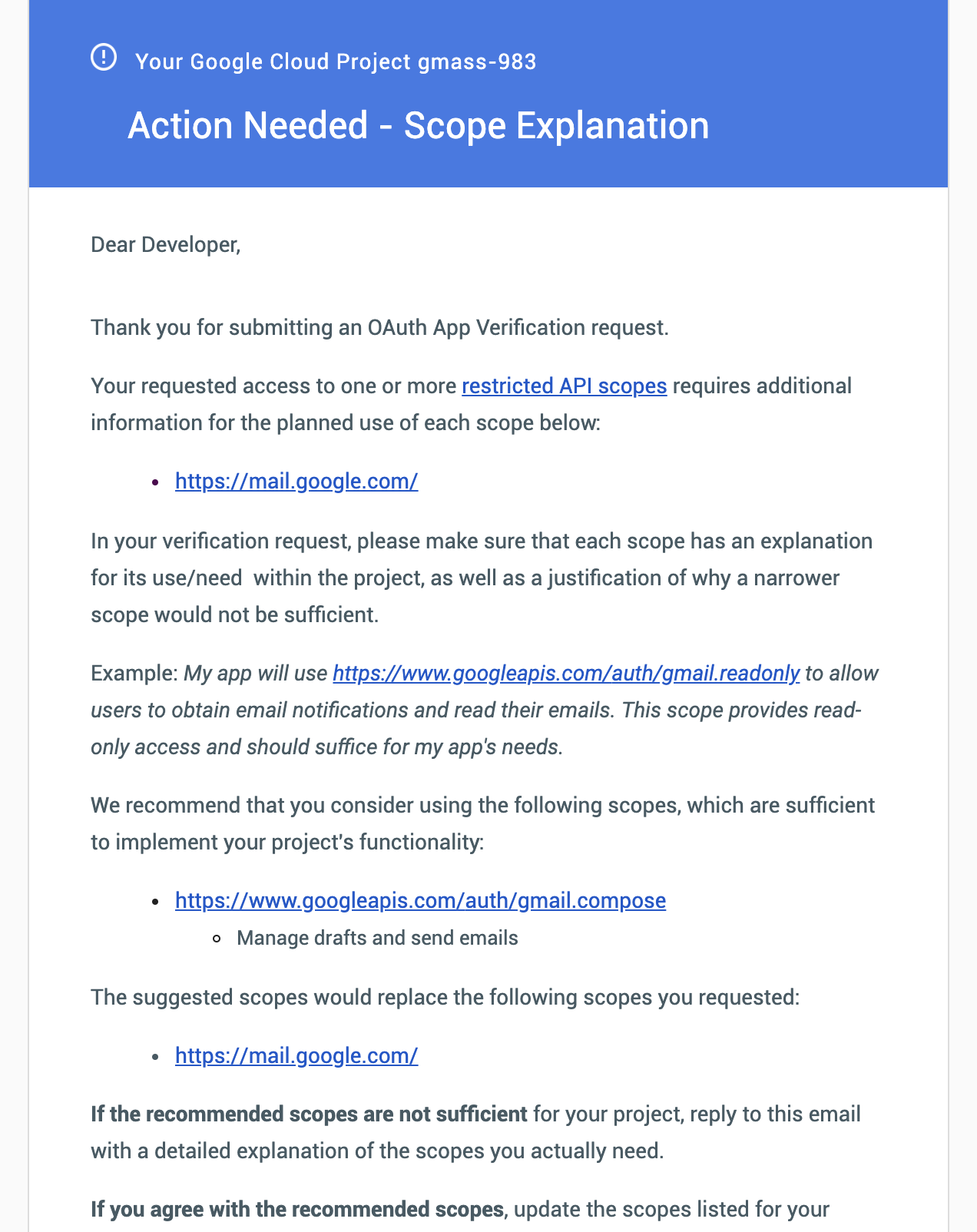
Google denies my request to skip the security assessment.
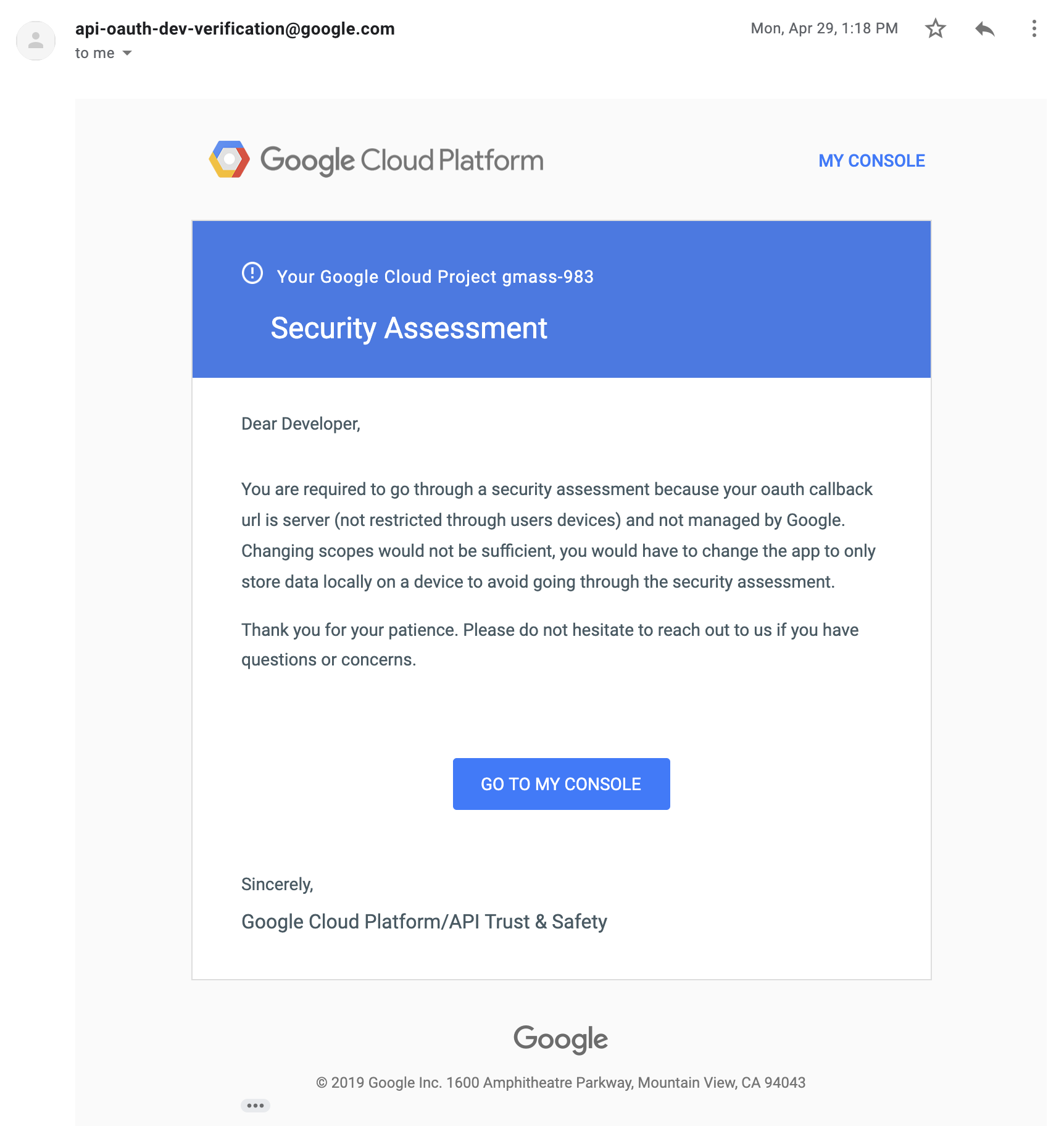
4/22/19
I respond to the notice asking if I can skip the security assessment if I reduce the Gmail API scopes I’m using for GMass.
4/20/19
I receive a notice from Google that the fun is only now beginning (proceed with security assessment).
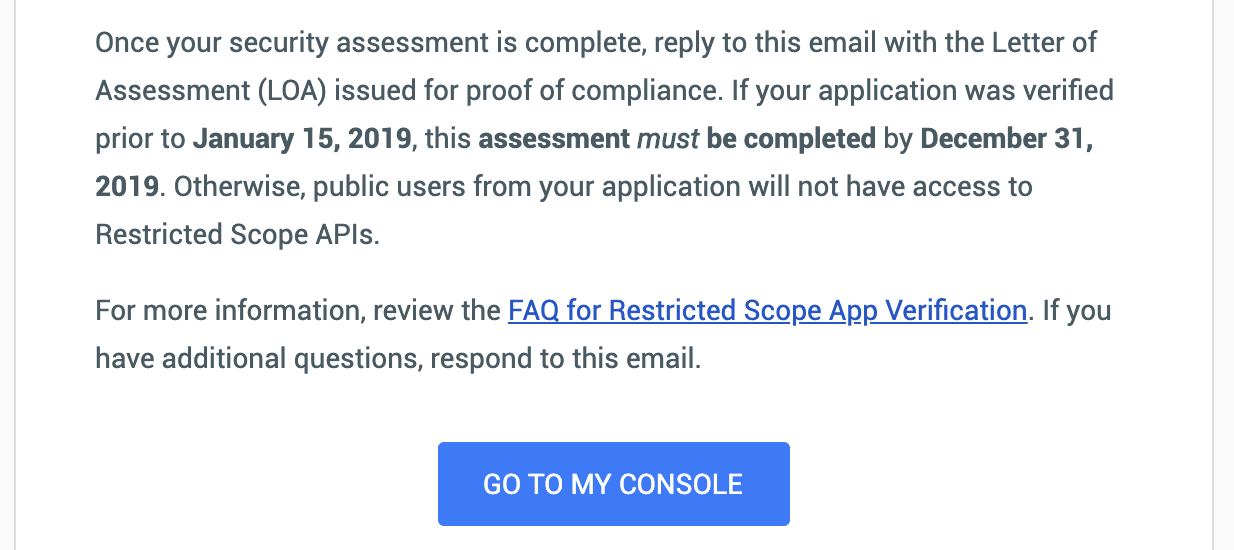
4/1/19
(April Fool’s Day — maybe they’ll let me know this has all been a joke?)
I’m told I’m in the final stages of verification.
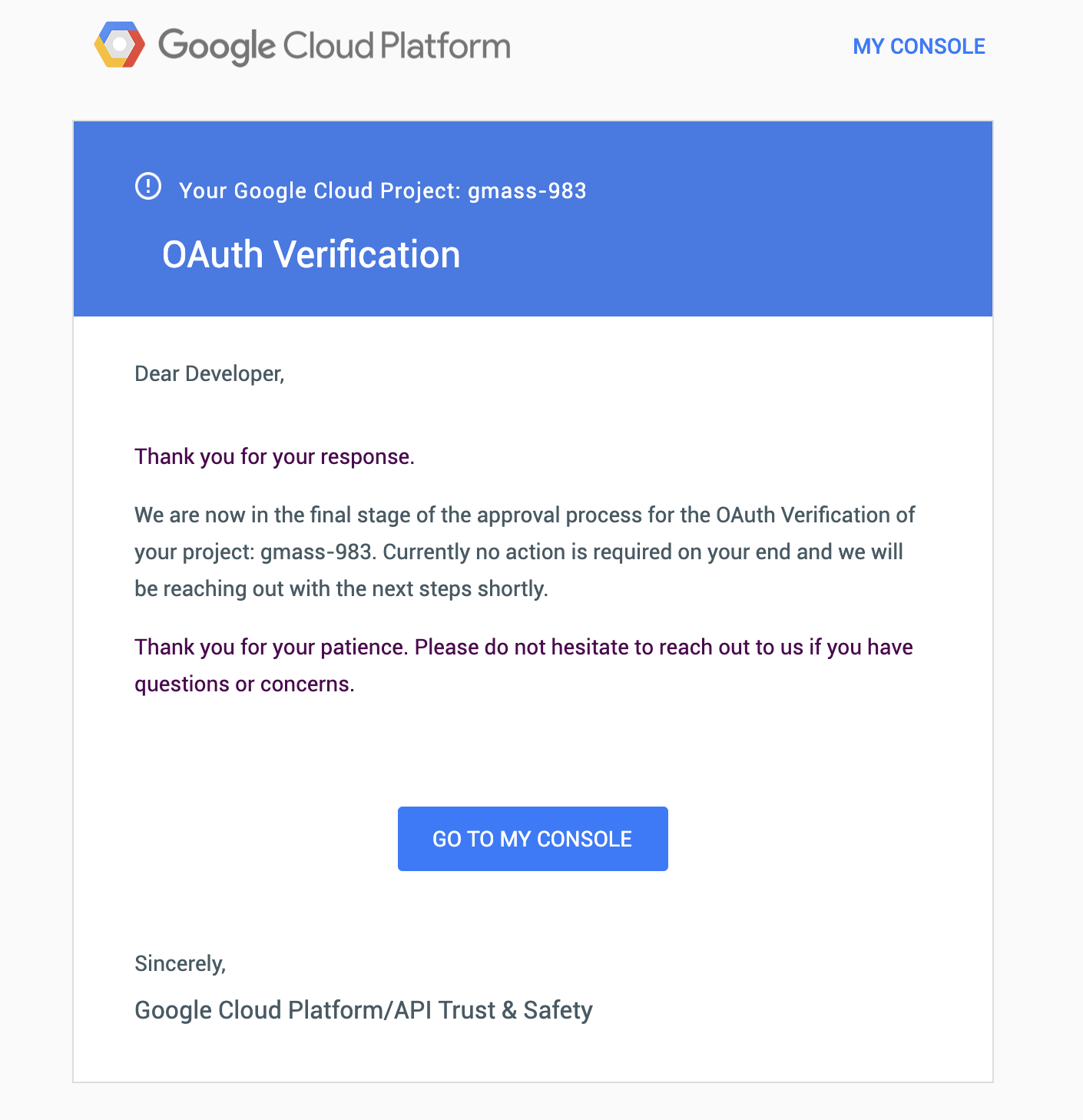
3/31/19
I respond with my agreement.

3/26/19
Google emails asking me to confirm my agreement with a statement.
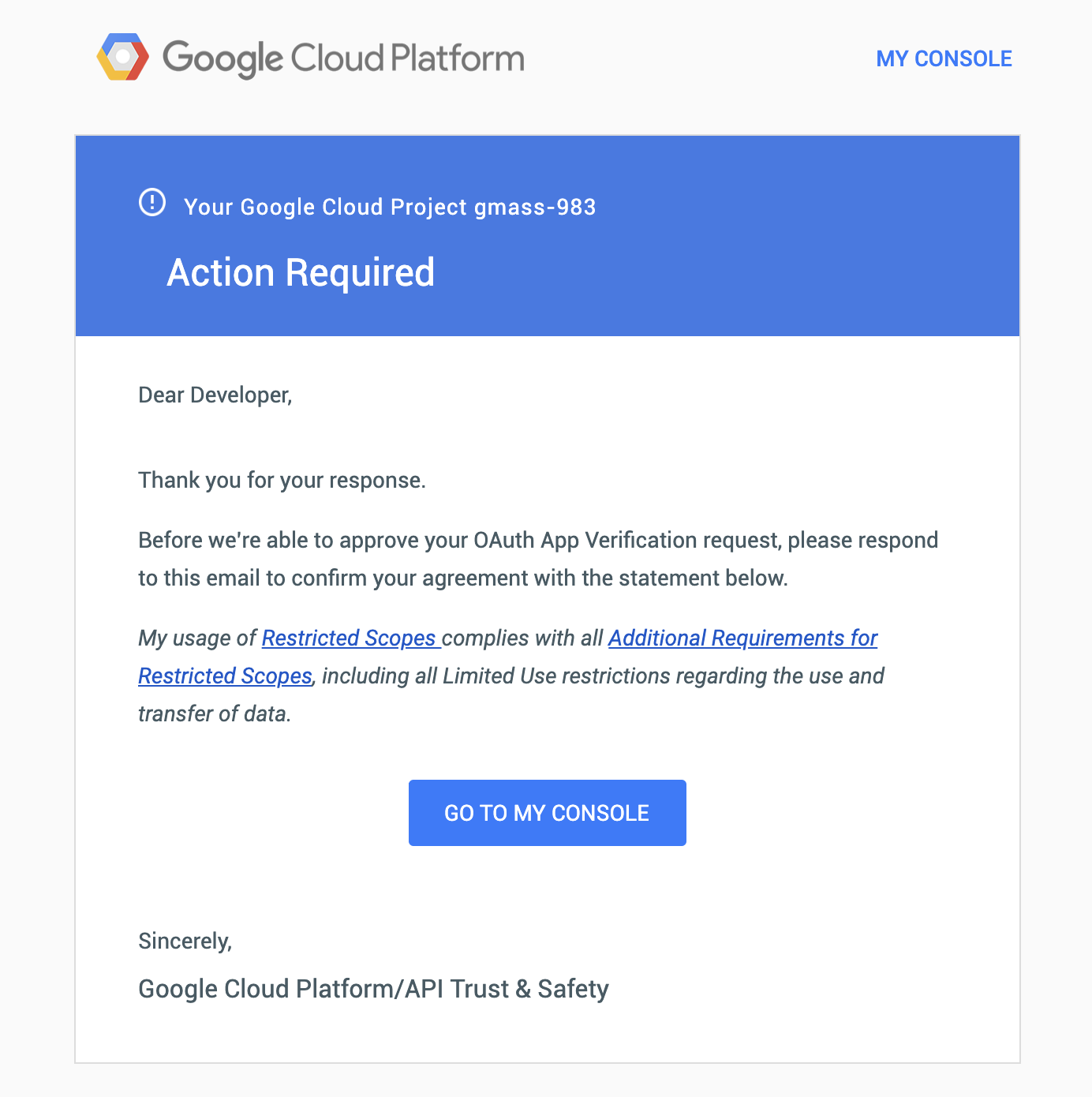
3/23/19
I responded with another video.
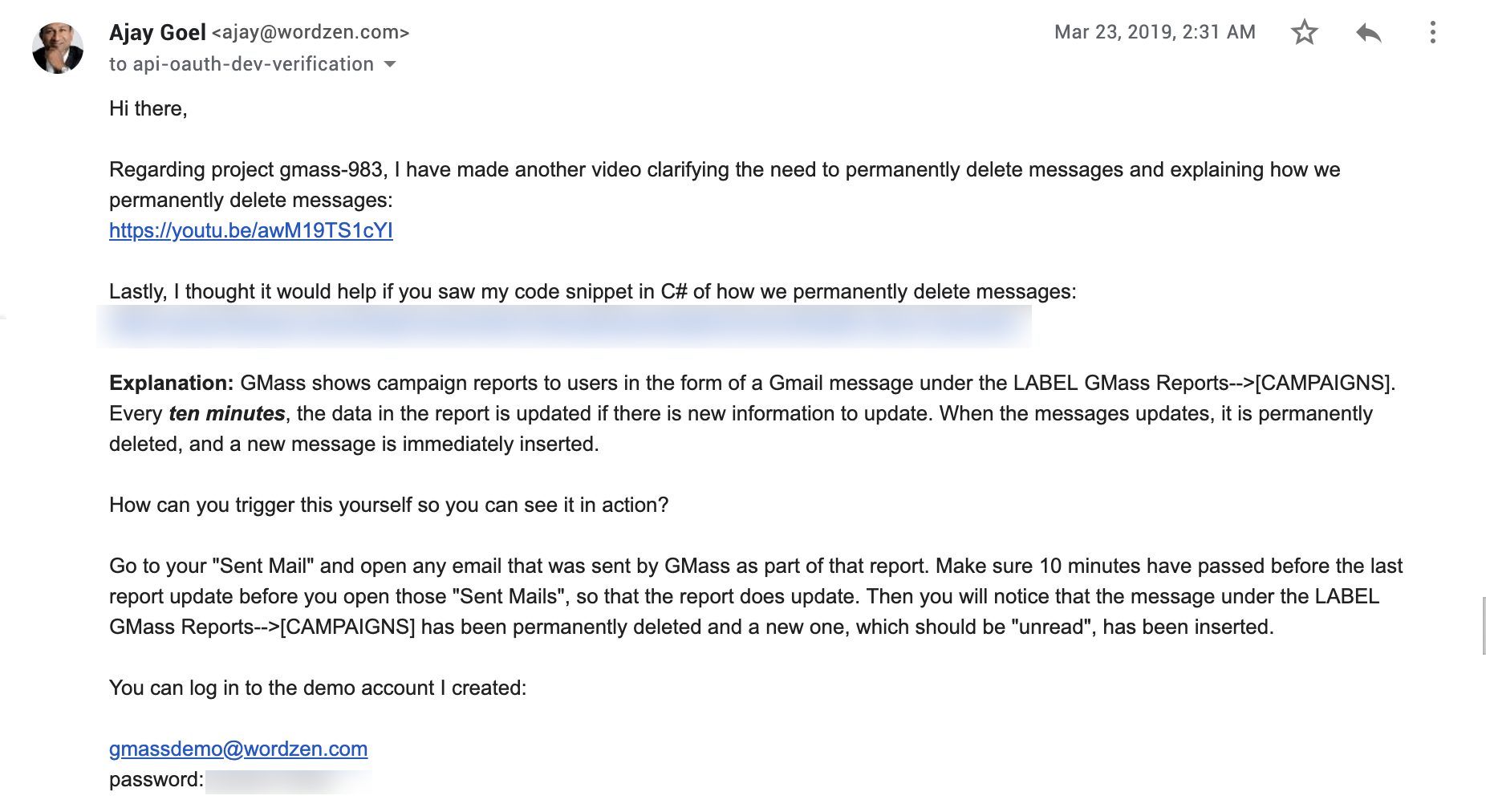
3/21/19 (a few hours later)
I received an additional request deeming the first video as insufficient.
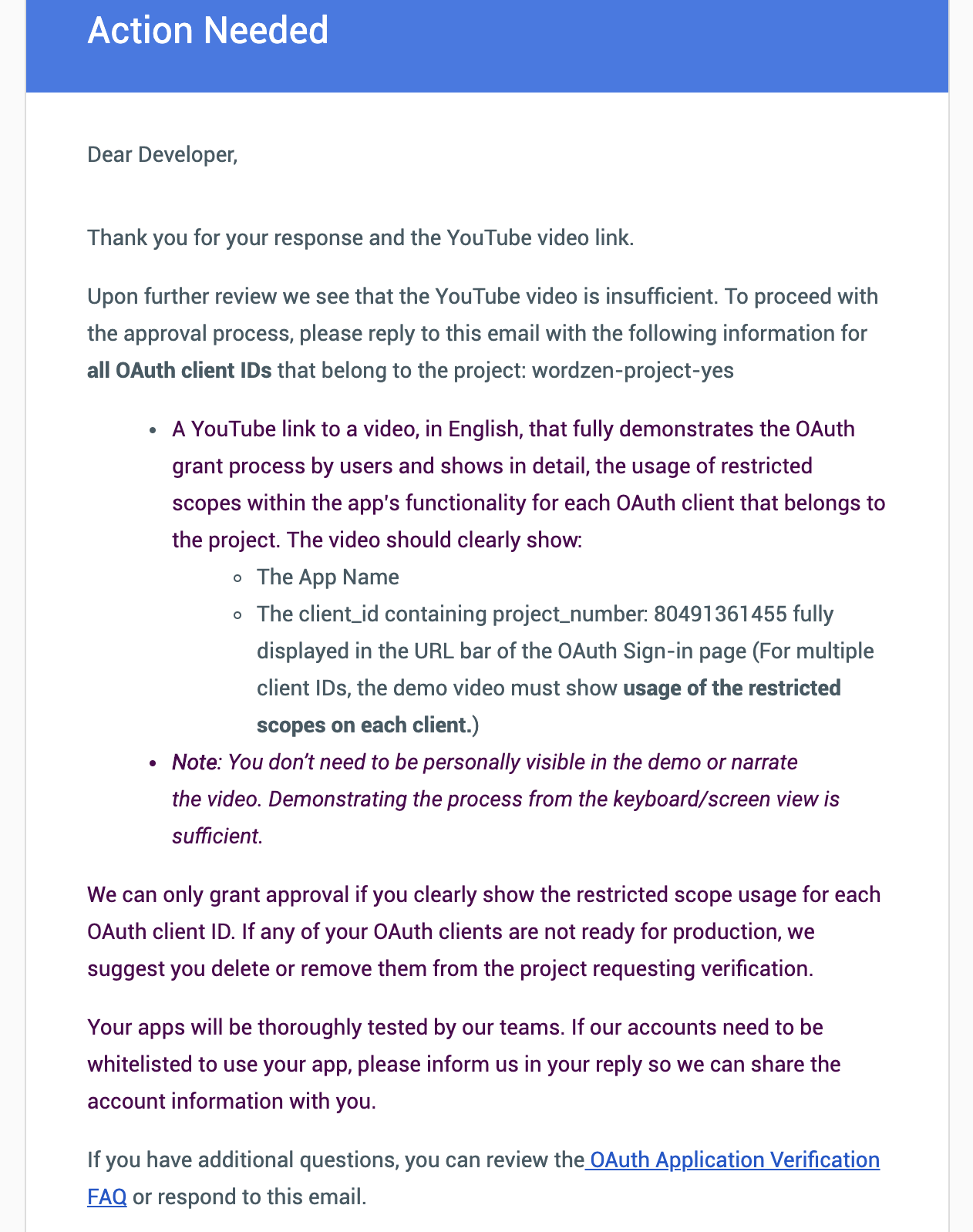
3/21/19
I receive this request from Google for an additional video.
3/18/19
I respond, letting Google know I’ve made the branding changes they suggested.
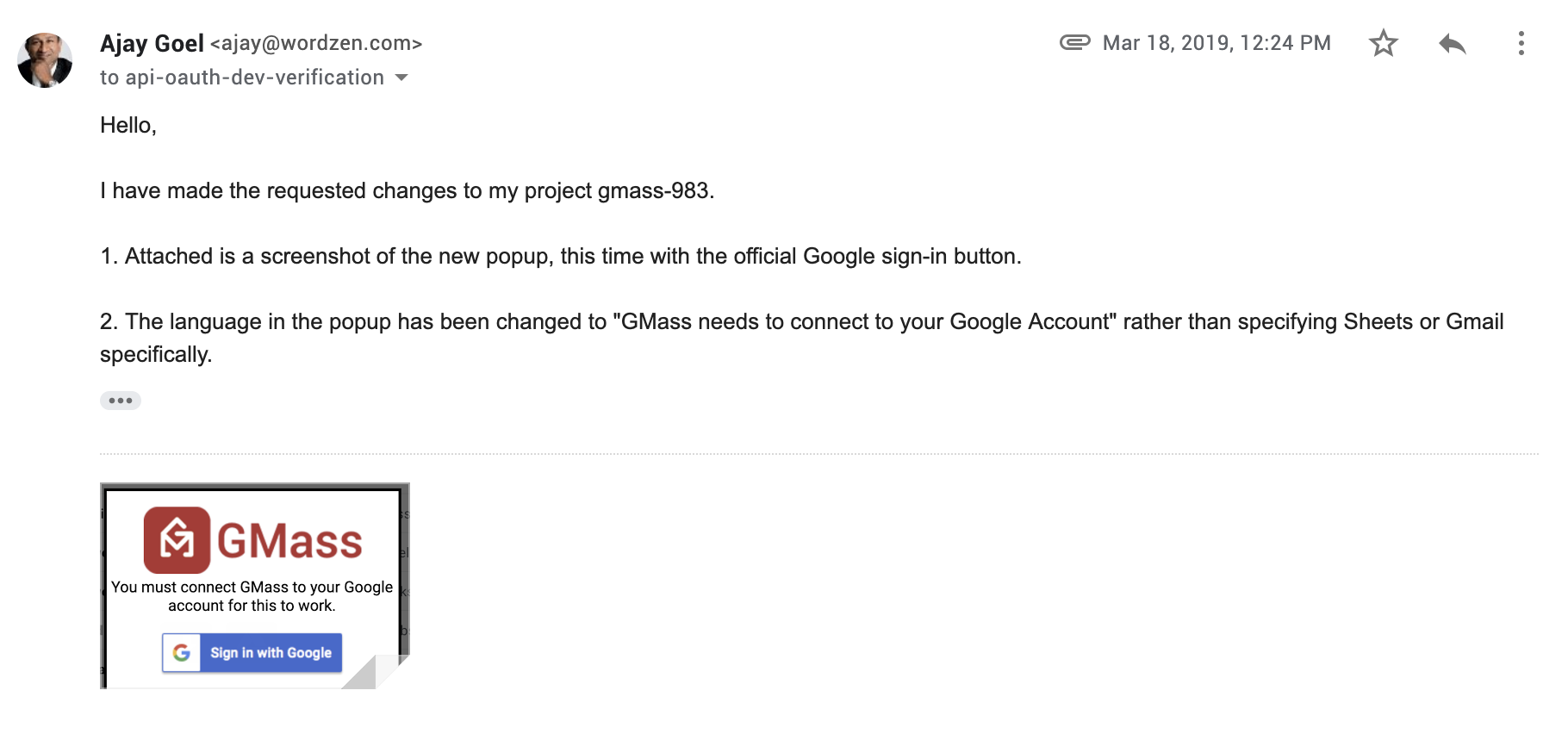
3/15/19
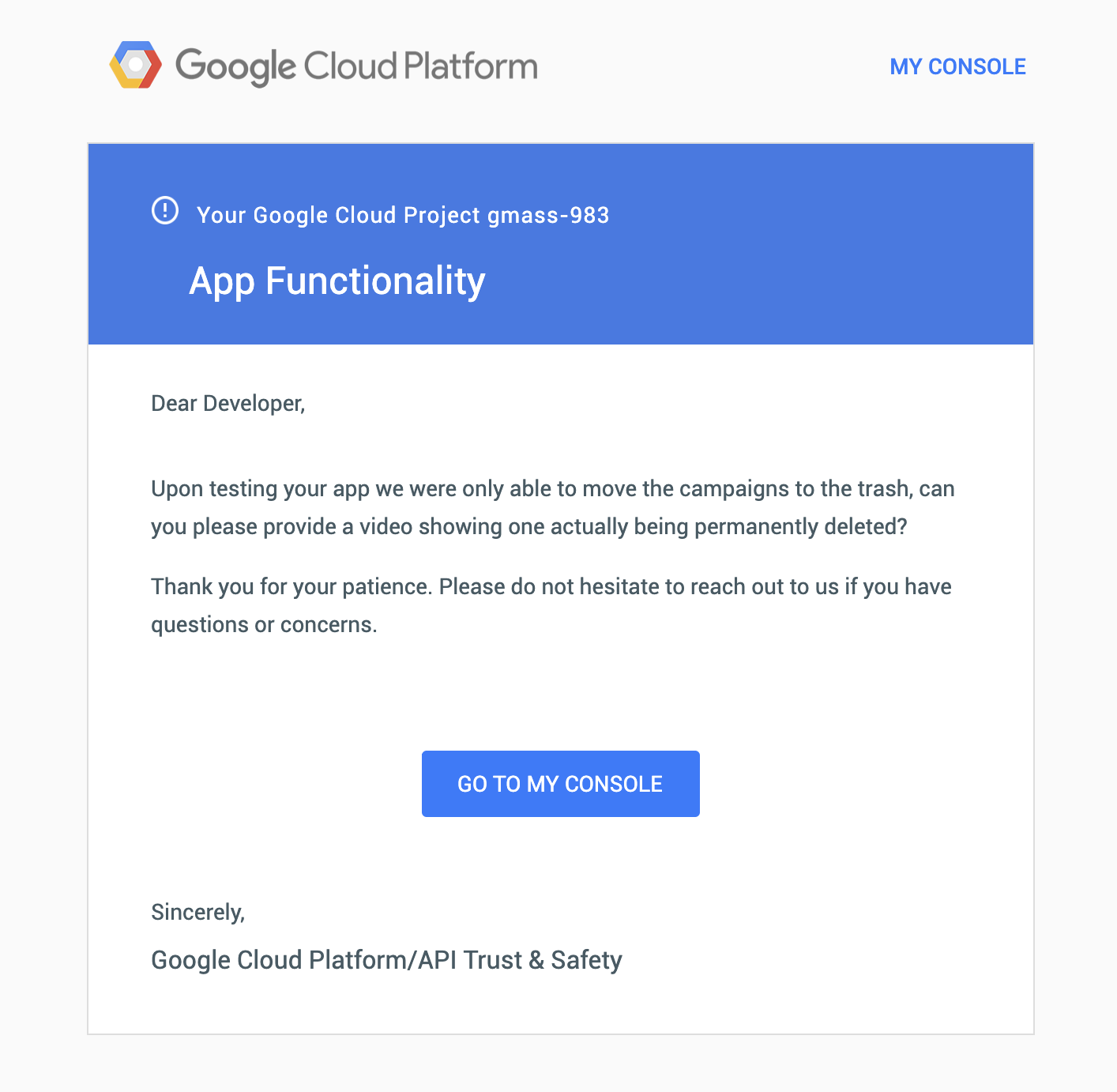
After Google presumably watches my video, they respond, asking them to conform to their branding guidelines.
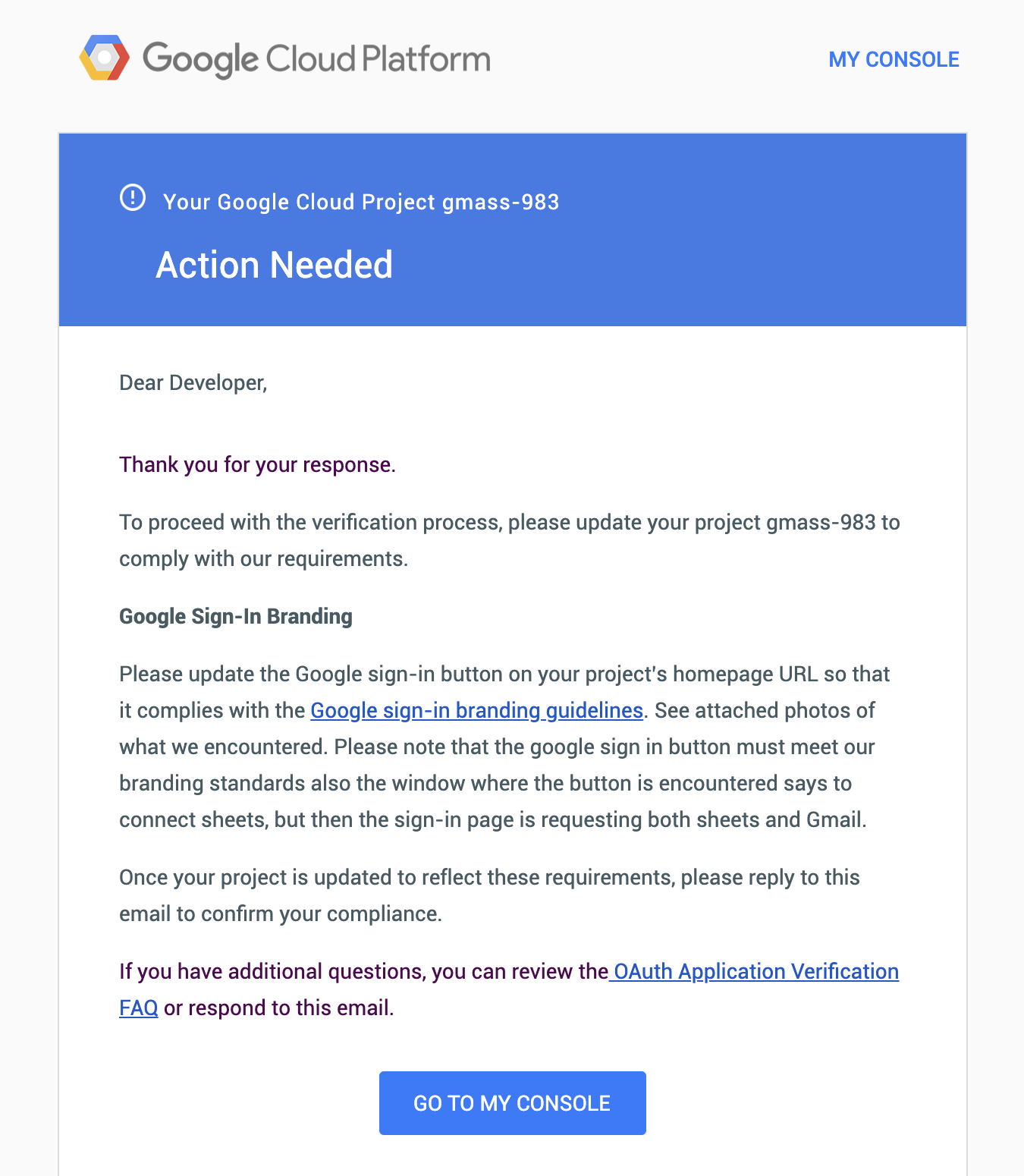
3/9/19
I respond with the requested YouTube video.
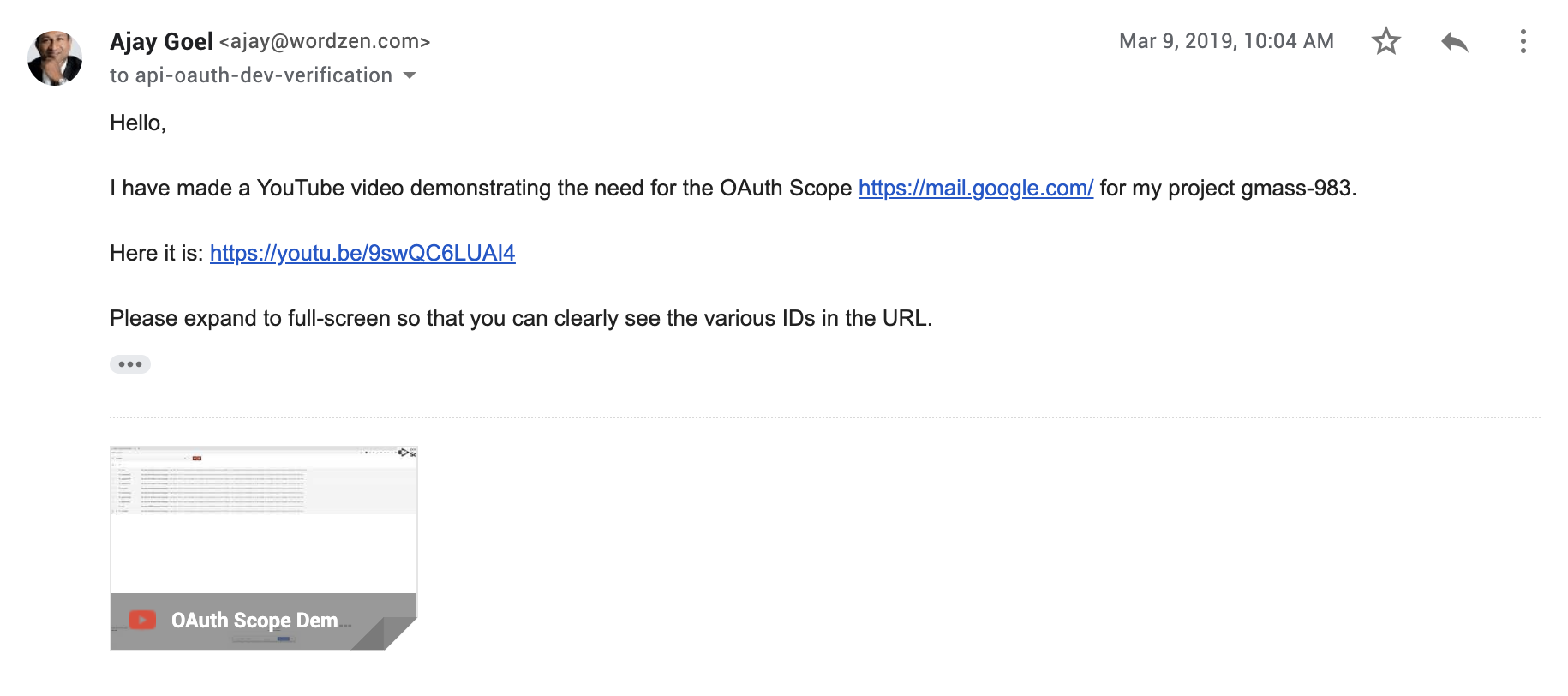
3/6/19
Google responds with their request for a YouTube video.
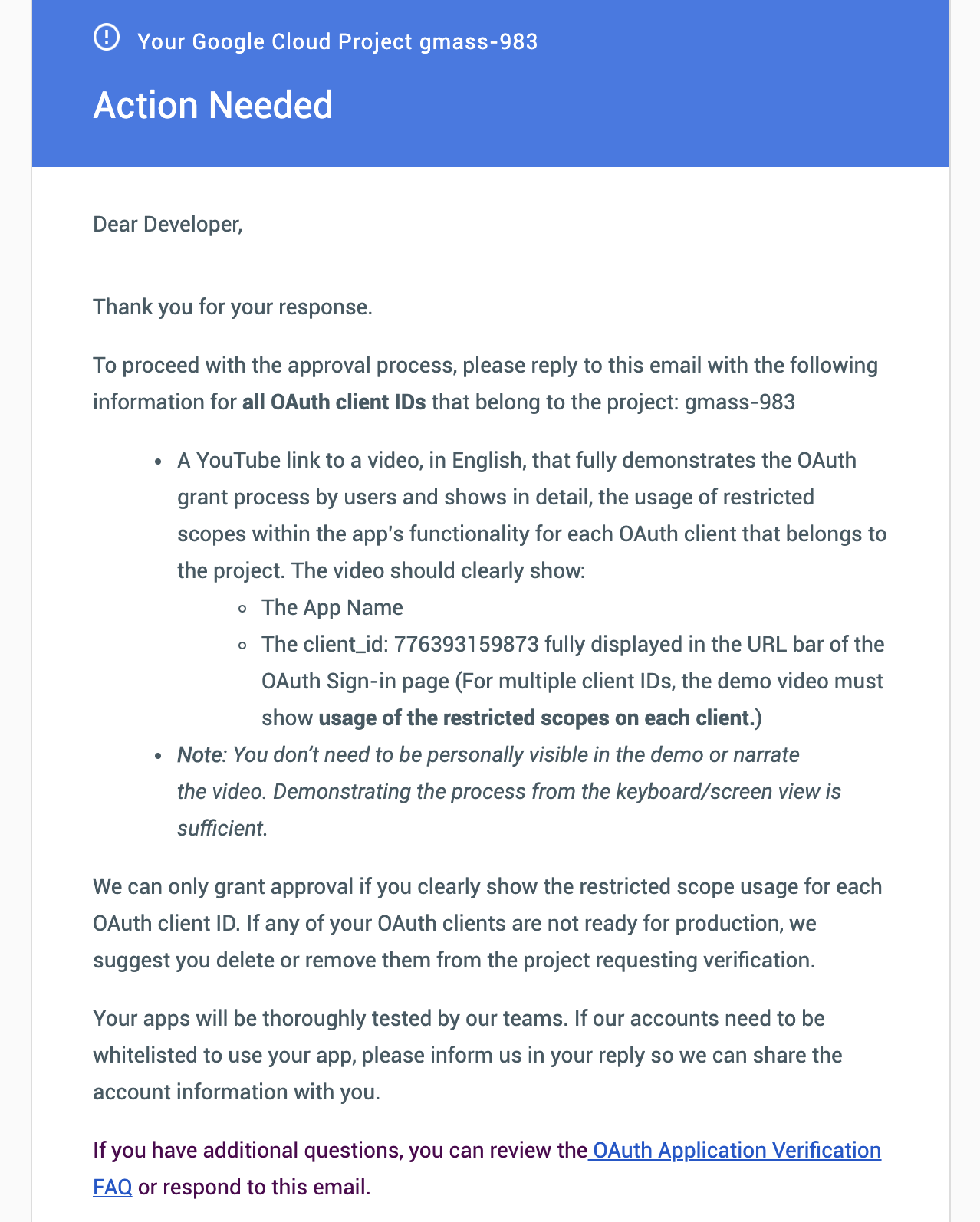
2/15/19
I responded to the ambiguous request from Google.
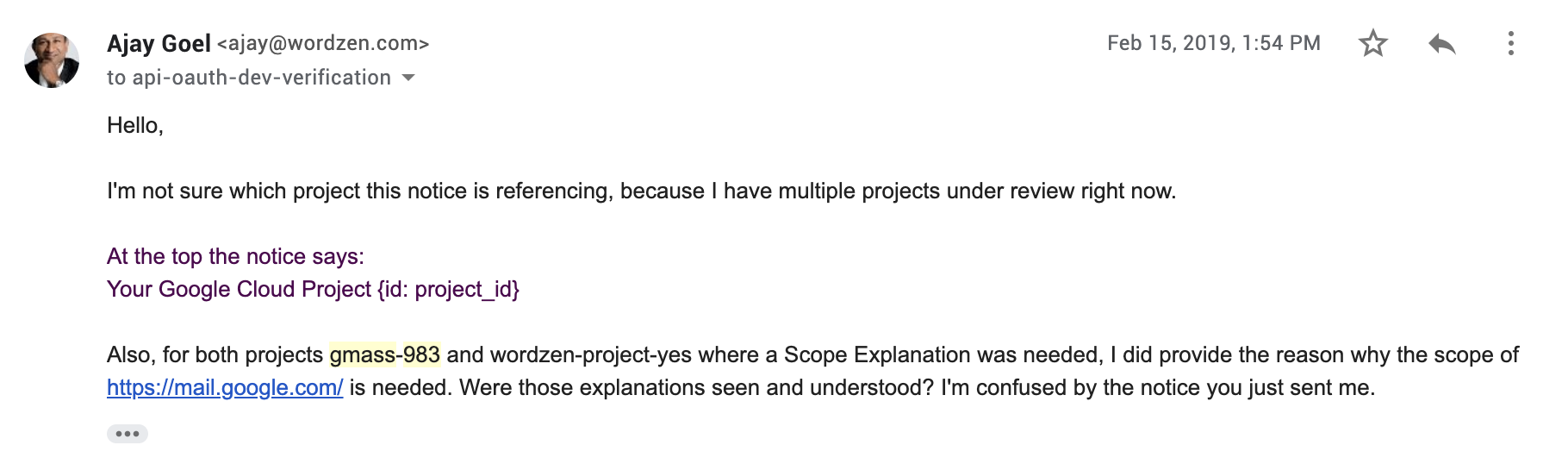
2/15/19
Received this email with no project ID listed, and given that I manage multiple apps built for Gmail, I didn’t know if this pertained to GMass or not.
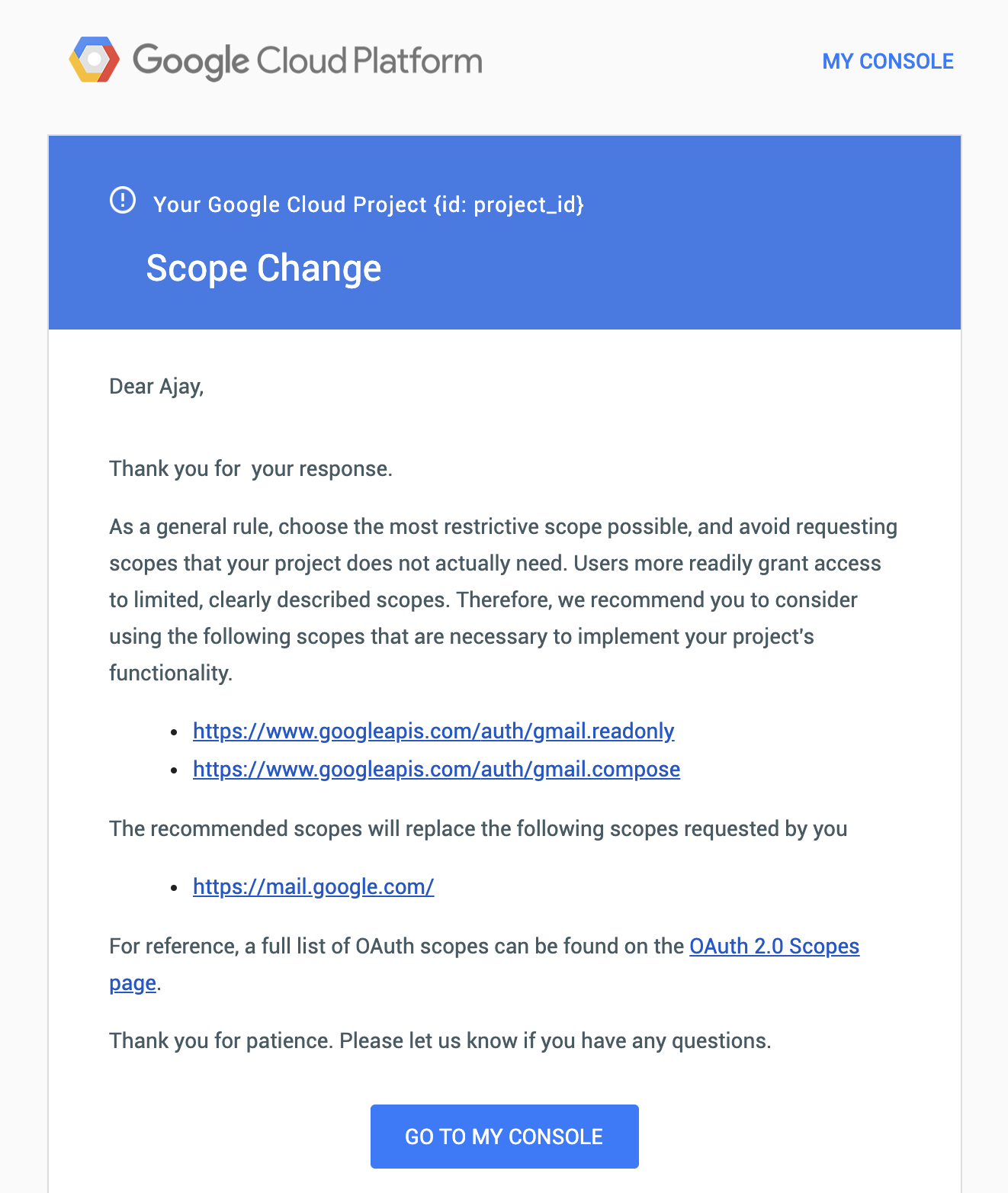
2/9/19
I respond to Google’s request for the scope explanation.
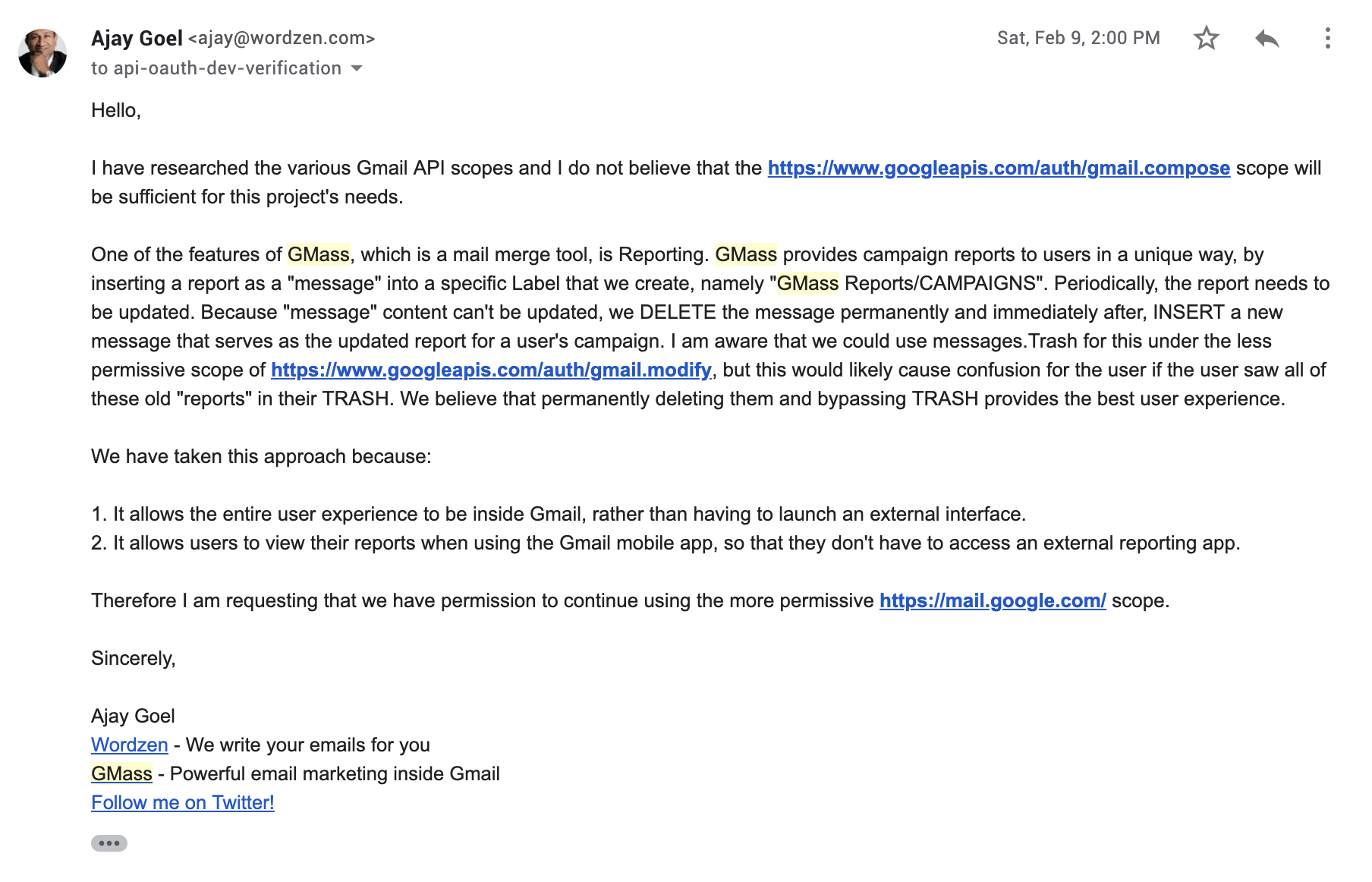
2/7/19
Email received from Google asking for an explanation of the need for the full mail.google.com scope
Email marketing, cold email, and mail merge all in one tool — that works inside Gmail
TRY GMASS FOR FREE
Download Chrome extension - 30 second install!
No credit card required


Hi Ajay & team, came across GMass. Looking for information on data security. Per this blog it seems like you are still working through being approved for Google’s new security requirements. If yes, do I need to wait before I use Gmass as there may be a threat to my gmail data if I connect to GMass today?
Vinay — no, you don’t need to wait for the assessment. It is safe to use GMass now.
“Amazing write-up!”
Thanks for sharing this good article, so useful article
“Great share!”
Great write up! waiting for the next update!
It’s also not clear how long this assessment is good for, will it be an annual review and what happens when you change the code accessing the gmail api?
Everything I’ve read indicates that this will be an annual process.
This is a wonderful write up, thanks for taking the time to do this.
Like you, I’ve had to go through the verification process and my heart sank when I first read the obtuse and confusing documentation and came across the 75k fee.
Fortunately my business falls under the local device only and I managed to get out of the security assessment and only do the video. But I can see how frustrating the whole thing is, you have my sympathies.
Lucky you! 🙂
I appreciate you taking the time to write this up – it is a frustrating experience to say the least.
I am curious about the email you received on 4-29. They say “Your callback URL is server (not restricted through users devices ) , and not managed by Google”. That seems to imply if you were using google servers, there would not be a problem.
And what does the ( not restricted through users devices ) mean? How would a server callback work that was “restricted” and therefor permissible?
My biggest complaint about this entire new process? Google doesn’t seem to give a fuck. The OAuth board on google is shut down, and you are pushed to stack exchange. Which I guess is fine if you have a code question – but it means you cannot even discuss the security audit or Google’s process – those are all Customer Relations issues. Everytime I’ve tried to discuss the issue there, my posts are closed.
We pay for gold tier GCP support – who will not answer any OAuth questions, much less provide advice or support on how to navigate this maze. I’m just a bit surprised at how quickly Google just kicked all the indie devs to the curb.
Hey — sorry for the late reply here.
1. That email on 4/29 — well, I don’t think that means that if I were to be hosted on the Google Cloud, rather than AWS where I am hosted, that I then wouldn’t have to go through the security assessment. I think because of the nature of my application posting OAuth data back to a server outside of the Google environment (for this purpose the Google Cloud is outside of the Google environment), I have to go through the assessment. Perhaps if my app were a Google Apps Script project, that’s what is meant by “managed by Google”.
2. Yea, I agree. They don’t give a f—. I do find that they do respond to my questions. If you have an email thread going with the OAuth team about the verification and security assessment, and you ask them a question, they will respond in time. Sometimes it takes a week, and sometimes the answer contradicts what you know to be true, so they aren’t putting their smartest people on the front lines.
I have to shut down my gmail app, too.
So sad.
Hello Ajay, what is the latest update on Google assessment?
Hey Mailtrack.io team! Nice to hear from you. See above for the latest updates. I’d love to hear how the process is going for you as well.
Hello,
GReat post! do you have an update?
I just updated the post with the last couple months of activity.
Hi,
Thanks for the post. Do you have an update on this?
I have been following this post for the past couple of months. Would be great if you can let us know the current status.
Thanks
Updates coming today.
Hi Ajay
Would you be willing to share the steps you took to secure your infrastructure prior to tests/quotes from Leviathan & Bishop Fox?
We are in the same general boat (AWS & similar gmail scopes used) and I’m looking to get ahead of the situation and make sure we are fully secured to their standards prior to an assessment.
So far I have modified various ssl & security settings on our webserver and have reached an “A” on a basic external scanning site like:
https://www.ssllabs.com/ssltest/
Hi Ajay,
I believe one of your inferences in the post on 5/16/19 is wrong – ” , if I don’t care about taking on @gmail.com users, then I don’t need to go through with the assessment. ” . If you uncheck the box corresponding to the the image you attached in that post, then only users of your domain will be able to view and install the application. You will not be able to publish the app to other Gsuite customers as well even if they own their own domain on Gsuite. In our use case, we don’t need to cater to .gmail users. We just want Gsuite users, but it is not possible without assessment. We too are starting the process and your blog is very helpful. Thank you .
Rgds
Robby
Relatas – Sales Intelligence
hi Ajay,
Where is the process at for you now? Also, why did you go with Leviathan after the SAQ was approved with Bishop Fox? Was it price? That part of the live update is unclear to me.
thanks so much for posting this. We need to go through this to bring in email data to a CRM – we’ve merged with a company with a more mature CRM platform and they are currently doing this.
oh my god,it will take a long time,sad 🙁
Ajay, thanks for the excellent article.
If there are others reading this post and going thru the audit process, I would like to get in touch with you. We are just about ready to engage one of the audit providers and I would like to get a feel for process, cost and your experience (even if the process is incomplete). Also if there are things that we can do to prepare for the audit and cut down the time (& cost 😉 . Any responses/feedback greatly appreciated.
You can email me directly at rajank -at- clariti -dot- app
TIA
Hi Ajay,
thanks a lot for documenting your journey here and taking all the trouble!
I am very interested in the “Self Assessment Questionnaire” part.
Would this be something that could be done completely instead of the full security assessment?
Is there a place to get more information about this questionnaire and when it is viable?
I hope you get through with this soon!
Best regards,
Fabian
Thank you so much for sharing this.
I ended up migrating my app to be desktop only (http://receiptrunner.com/) but I’m thinking of making a web version again now that it’s starting to get traction.
The only google data I’d need to store or handle serverside would be stuff in a database, and I could end up using something like Firebase. Presumably the security check then would only take a few minutes, as nothing would be sent except to Firebase (a google product) using Firebase APIs.
You said you ended up paying for 3 days worth of work, but can’t comment on the hourly price. That’s fair – but can you say if you spent considerably less than the 15k USD minimum they stated, or did it cap out at the minimum so that you have do pay 15k – no matter how easy the security assessment is?
I’m interested to know if the process can cost less than 15k if it’s super easy for Leviathan.
Best,
Daniel
I’m Thinh from Relotalent
Thanks for sharing this good article, so useful article.
We have same problem with new process of google oauth verification and security.
Really stressed
Curious what decisions you have made regarding the annual security requirement since 2019. We have similarly gone through the process in early 2020 and early 2021. As we consider the early 2022 period, we note the assessment fees are steadily increasing 20% annually, despite the scope remaining unchanged, and our robust ISMS with ISO27001 and SOC2 type 2 audits. As has been pointed out many times, it does not seem the requirement and the costs are aligned.